How Is the Development Process for the Bitcoin Core Client Managed?
The development of the Bitcoin Core client is a cornerstone of maintaining the security, stability, and innovation within the Bitcoin network. As an open-source project, it relies heavily on a community-driven approach that emphasizes transparency and collaborative effort. Anyone with programming skills can contribute to its codebase, which fosters a diverse pool of developers from around the world. This inclusivity ensures that multiple perspectives are considered when implementing new features or fixing bugs.
The process begins with proposals for changes known as Bitcoin Improvement Proposals (BIPs). These are detailed documents suggesting modifications to enhance functionality or security. Once a BIP is drafted, it undergoes rigorous review by experienced developers through pull requests on GitHub—a platform central to managing contributions. Each proposed change must pass thorough code reviews to ensure adherence to quality standards and prevent vulnerabilities.
Bitcoin Core follows a structured release cycle typically every six months. This regular schedule allows for systematic updates that include bug fixes, performance improvements, and sometimes new features like privacy enhancements or scalability solutions. Before any release goes live, comprehensive testing—both automated and manual—is conducted across various environments to verify stability and security integrity.
Continuous integration tools play an essential role in early detection of issues during development stages. They automatically run tests whenever code changes are submitted, helping maintain high-quality standards throughout the project lifecycle. The collaborative nature combined with disciplined processes ensures that Bitcoin Core remains robust against potential threats while evolving in response to technological advancements.
Funding Mechanisms Supporting Bitcoin Core Development
Sustaining ongoing development efforts requires significant financial resources; however, unlike many proprietary software projects, Bitcoin Core relies predominantly on community-based funding models rather than corporate sponsorships alone. Donations from individual users form one of its primary income streams—these voluntary contributions help cover operational costs such as server hosting and developer stipends.
In addition to direct donations from enthusiasts worldwide, grants also play an important role in supporting specific initiatives within the project’s roadmap. Various organizations dedicated to advancing blockchain technology provide targeted funding for research or feature implementation efforts aligned with their strategic goals.
Corporate sponsorships further bolster development capacity by financially supporting key contributors who work full-time on core improvements. Notable companies like Blockstream and Chaincode Labs sponsor individual developers or entire teams involved in critical areas such as scalability upgrades or security enhancements—this model helps attract talent capable of handling complex technical challenges efficiently.
Bitcoin Improvement Proposals (BIPs) often require substantial resources when they introduce significant protocol changes—for example, upgrades like Taproot—which improve transaction privacy and efficiency have been funded through this combination of donations and sponsorships over recent years.
Recent Developments Shaping Bitcoin Core’s Future
Over recent years, several major upgrades have marked milestones in enhancing Bitcoin's capabilities through core development efforts backed by community support:
Taproot Upgrade (2021): One of the most notable advancements was implementing Taproot—a protocol upgrade designed to improve transaction privacy while increasing scalability options on-chain. Its successful deployment was made possible through coordinated community funding efforts involving both donations from users keen on improving network efficiency—and sponsorships from organizations committed to long-term sustainability.
SegWit2x Controversy: In 2017 there was significant debate surrounding SegWit2x—a proposed hard fork intended initially for increasing block size limits—but faced opposition due mainly to concerns about decentralization risks and security implications among different stakeholder groups within the ecosystem leading ultimately toward abandonment in favor of Segregated Witness (SegWit). This episode underscored how community consensus—or lack thereof—can influence development trajectories.
Lightning Network Integration: Ongoing work aims at integrating off-chain solutions like Lightning Network into core software infrastructure—to facilitate faster transactions at lower fees without congesting main chain blocks—highlighting continuous innovation driven by collaborative effort.
Security Enhancements: The team actively works on fortifying wallet management systems against emerging threats such as 51% attacks while improving resistance mechanisms overall—a vital aspect given cryptocurrency's value proposition as digital gold.
These developments exemplify how collective input—from volunteers’ coding contributions supported by organizational backing—drives forward-looking improvements aligned with user needs for increased privacy, speed, safety—and broader adoption potential.
Challenges Facing Development Funding & Community Dynamics
Despite its strengths rooted in openness and collaboration—the decentralized nature introduces unique challenges:
Community Disagreements: Divergent opinions among stakeholders regarding technical directions can cause delays or fragmentation within development teams—as seen during controversies like SegWit2x—that may hinder timely progress.
Funding Uncertainty: Heavy reliance on voluntary donations means fluctuations can impact resource availability; if donor interest wanes or organizational priorities shift away from supporting core devs financially—project momentum might slow down.
Regulatory Pressures: As governments worldwide tighten regulations around cryptocurrencies—including anti-money laundering measures—they could impose restrictions affecting donation channels or create legal uncertainties impacting open-source projects’ operations globally.
Addressing these issues requires transparent governance structures coupled with diversified funding strategies—including institutional partnerships—to ensure resilience amid evolving external pressures.
How Open Source Principles Ensure Security & Transparency
One key reason behind Bitcoin’s resilience lies in its open-source foundation: anyone can scrutinize source code for vulnerabilities; this transparency fosters trustworthiness crucial for financial systems handling billions worth of assets daily. Regular peer reviews enable rapid identification—and patching—of bugs before exploitation occurs; this collective vigilance enhances overall network robustness over time.
Furthermore: active engagement from global developer communities accelerates innovation cycles while maintaining high-security standards necessary under E-A-T principles (Expertise–Authoritativeness–Trustworthiness). By openly sharing updates via repositories like GitHub—and documenting decision-making processes transparently—the project builds credibility among users ranging from casual investors up through institutional stakeholders seeking reliable infrastructure.
Future Outlook: Sustaining Innovation Amid Challenges
Looking ahead involves balancing continuous technological advancement with sustainable funding models amidst regulatory landscapes shifting globally:
- Increasing integration between Lightning Network solutions promises faster payments suitable even for microtransactions
- Privacy-focused features will likely remain priorities given rising demand
- Efforts toward decentralizing governance could mitigate risks associated with concentrated influence
To sustain momentum:
- Maintaining diverse sources of support—including grants alongside donations—is essential
- Fostering inclusive participation across geographies enhances resilience
- Emphasizing transparent decision-making aligns well with user expectations rooted in trust
By adhering closely to open-source best practices combined with innovative technical roadmaps supported by broad-based backing—all underpinned by strong ethical standards—the future looks promising despite inevitable hurdles.
This overview provides clarity into how foundational principles shape ongoing developments within Bitcoin Core—from management practices grounded in transparency & collaboration—to funding strategies ensuring sustained growth amid external pressures—all vital components underpinning one of today’s most influential blockchain projects worldwide


JCUSER-F1IIaxXA
2025-05-11 06:09
How is the development process for the Bitcoin (BTC) Core client managed and funded?
How Is the Development Process for the Bitcoin Core Client Managed?
The development of the Bitcoin Core client is a cornerstone of maintaining the security, stability, and innovation within the Bitcoin network. As an open-source project, it relies heavily on a community-driven approach that emphasizes transparency and collaborative effort. Anyone with programming skills can contribute to its codebase, which fosters a diverse pool of developers from around the world. This inclusivity ensures that multiple perspectives are considered when implementing new features or fixing bugs.
The process begins with proposals for changes known as Bitcoin Improvement Proposals (BIPs). These are detailed documents suggesting modifications to enhance functionality or security. Once a BIP is drafted, it undergoes rigorous review by experienced developers through pull requests on GitHub—a platform central to managing contributions. Each proposed change must pass thorough code reviews to ensure adherence to quality standards and prevent vulnerabilities.
Bitcoin Core follows a structured release cycle typically every six months. This regular schedule allows for systematic updates that include bug fixes, performance improvements, and sometimes new features like privacy enhancements or scalability solutions. Before any release goes live, comprehensive testing—both automated and manual—is conducted across various environments to verify stability and security integrity.
Continuous integration tools play an essential role in early detection of issues during development stages. They automatically run tests whenever code changes are submitted, helping maintain high-quality standards throughout the project lifecycle. The collaborative nature combined with disciplined processes ensures that Bitcoin Core remains robust against potential threats while evolving in response to technological advancements.
Funding Mechanisms Supporting Bitcoin Core Development
Sustaining ongoing development efforts requires significant financial resources; however, unlike many proprietary software projects, Bitcoin Core relies predominantly on community-based funding models rather than corporate sponsorships alone. Donations from individual users form one of its primary income streams—these voluntary contributions help cover operational costs such as server hosting and developer stipends.
In addition to direct donations from enthusiasts worldwide, grants also play an important role in supporting specific initiatives within the project’s roadmap. Various organizations dedicated to advancing blockchain technology provide targeted funding for research or feature implementation efforts aligned with their strategic goals.
Corporate sponsorships further bolster development capacity by financially supporting key contributors who work full-time on core improvements. Notable companies like Blockstream and Chaincode Labs sponsor individual developers or entire teams involved in critical areas such as scalability upgrades or security enhancements—this model helps attract talent capable of handling complex technical challenges efficiently.
Bitcoin Improvement Proposals (BIPs) often require substantial resources when they introduce significant protocol changes—for example, upgrades like Taproot—which improve transaction privacy and efficiency have been funded through this combination of donations and sponsorships over recent years.
Recent Developments Shaping Bitcoin Core’s Future
Over recent years, several major upgrades have marked milestones in enhancing Bitcoin's capabilities through core development efforts backed by community support:
Taproot Upgrade (2021): One of the most notable advancements was implementing Taproot—a protocol upgrade designed to improve transaction privacy while increasing scalability options on-chain. Its successful deployment was made possible through coordinated community funding efforts involving both donations from users keen on improving network efficiency—and sponsorships from organizations committed to long-term sustainability.
SegWit2x Controversy: In 2017 there was significant debate surrounding SegWit2x—a proposed hard fork intended initially for increasing block size limits—but faced opposition due mainly to concerns about decentralization risks and security implications among different stakeholder groups within the ecosystem leading ultimately toward abandonment in favor of Segregated Witness (SegWit). This episode underscored how community consensus—or lack thereof—can influence development trajectories.
Lightning Network Integration: Ongoing work aims at integrating off-chain solutions like Lightning Network into core software infrastructure—to facilitate faster transactions at lower fees without congesting main chain blocks—highlighting continuous innovation driven by collaborative effort.
Security Enhancements: The team actively works on fortifying wallet management systems against emerging threats such as 51% attacks while improving resistance mechanisms overall—a vital aspect given cryptocurrency's value proposition as digital gold.
These developments exemplify how collective input—from volunteers’ coding contributions supported by organizational backing—drives forward-looking improvements aligned with user needs for increased privacy, speed, safety—and broader adoption potential.
Challenges Facing Development Funding & Community Dynamics
Despite its strengths rooted in openness and collaboration—the decentralized nature introduces unique challenges:
Community Disagreements: Divergent opinions among stakeholders regarding technical directions can cause delays or fragmentation within development teams—as seen during controversies like SegWit2x—that may hinder timely progress.
Funding Uncertainty: Heavy reliance on voluntary donations means fluctuations can impact resource availability; if donor interest wanes or organizational priorities shift away from supporting core devs financially—project momentum might slow down.
Regulatory Pressures: As governments worldwide tighten regulations around cryptocurrencies—including anti-money laundering measures—they could impose restrictions affecting donation channels or create legal uncertainties impacting open-source projects’ operations globally.
Addressing these issues requires transparent governance structures coupled with diversified funding strategies—including institutional partnerships—to ensure resilience amid evolving external pressures.
How Open Source Principles Ensure Security & Transparency
One key reason behind Bitcoin’s resilience lies in its open-source foundation: anyone can scrutinize source code for vulnerabilities; this transparency fosters trustworthiness crucial for financial systems handling billions worth of assets daily. Regular peer reviews enable rapid identification—and patching—of bugs before exploitation occurs; this collective vigilance enhances overall network robustness over time.
Furthermore: active engagement from global developer communities accelerates innovation cycles while maintaining high-security standards necessary under E-A-T principles (Expertise–Authoritativeness–Trustworthiness). By openly sharing updates via repositories like GitHub—and documenting decision-making processes transparently—the project builds credibility among users ranging from casual investors up through institutional stakeholders seeking reliable infrastructure.
Future Outlook: Sustaining Innovation Amid Challenges
Looking ahead involves balancing continuous technological advancement with sustainable funding models amidst regulatory landscapes shifting globally:
- Increasing integration between Lightning Network solutions promises faster payments suitable even for microtransactions
- Privacy-focused features will likely remain priorities given rising demand
- Efforts toward decentralizing governance could mitigate risks associated with concentrated influence
To sustain momentum:
- Maintaining diverse sources of support—including grants alongside donations—is essential
- Fostering inclusive participation across geographies enhances resilience
- Emphasizing transparent decision-making aligns well with user expectations rooted in trust
By adhering closely to open-source best practices combined with innovative technical roadmaps supported by broad-based backing—all underpinned by strong ethical standards—the future looks promising despite inevitable hurdles.
This overview provides clarity into how foundational principles shape ongoing developments within Bitcoin Core—from management practices grounded in transparency & collaboration—to funding strategies ensuring sustained growth amid external pressures—all vital components underpinning one of today’s most influential blockchain projects worldwide
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🚀 The Future of Bitcoin is closer than you think!
By 2030, Bitcoin could transform the financial world as we know it. Whether you’re a seasoned HODLer or just starting your crypto journey, the question is… how many will YOU own?


JuCoin Media
2025-08-13 14:49
The Future of Bitcoin 🚀 – How Many Will You Own by 2030?
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What is the Funding Rate in Perpetual Futures?
The funding rate is a fundamental concept in perpetual futures trading, especially within cryptocurrency markets. It acts as a mechanism to keep the price of perpetual contracts aligned with the underlying asset's spot price. Unlike traditional futures, which have fixed expiration dates, perpetual futures are designed to trade indefinitely. This unique feature necessitates a system—namely, the funding rate—to maintain market stability and liquidity over time.
In essence, the funding rate represents periodic payments exchanged between traders holding long and short positions based on prevailing market conditions. When used correctly, it helps prevent significant deviations between the futures contract price and the actual market value of the underlying asset.
How Does the Funding Rate Work?
The primary purpose of the funding rate is to balance supply and demand within perpetual futures markets. It operates on a regular schedule—often every 8 hours—where traders either pay or receive fees depending on their position type (long or short) and current market dynamics.
If traders collectively believe that prices will rise above spot prices, long positions tend to dominate. To prevent excessive divergence from real-world prices, exchanges implement a positive funding rate where longs pay shorts periodically. Conversely, if futures prices fall below spot prices due to bearish sentiment or other factors, negative funding rates may occur where shorts pay longs.
This payment flow incentivizes traders' behavior: high positive rates encourage some longs to close their positions or take profits while attracting more shorts; negative rates do just the opposite by encouraging longs to hold onto their positions despite unfavorable conditions.
Calculation of Funding Rates
Understanding how funding rates are calculated provides insight into their role in maintaining equilibrium:
- Basis Difference: The core component involves calculating the difference between current spot prices and futures contract prices.
- Interest Rate Component: Some models incorporate an interest component reflecting borrowing costs.
- Premium/Discount Adjustment: The calculation considers whether contracts are trading at a premium (above spot) or discount (below spot).
Most exchanges compute this rate every 8 hours using real-time data from both markets. The formula varies slightly across platforms but generally follows this pattern:
Funding Rate = (Futures Price - Spot Price) / Spot Price * Adjustment FactorWhere adjustments account for interest rates and other market factors specific to each exchange’s methodology.
Why Is The Funding Rate Important for Traders?
For traders engaged in perpetual futures trading, understanding how funding impacts profitability is crucial:
- Cost Management: A positive funding rate means holding long positions incurs periodic costs; negative rates mean short sellers face similar charges.
- Strategy Planning: Anticipating changes in fundings can influence entry/exit points—for example, avoiding entering new long positions when high positive rates are expected.
- Risk Control: Sudden spikes or drops in fundings often signal shifts in market sentiment or volatility; monitoring these can help mitigate potential losses.
Moreover, since these payments happen automatically at scheduled intervals through exchange mechanisms like wallet deductions or credits, they directly affect net gains/losses over time.
Impact of Market Volatility on Funding Rates
Market volatility significantly influences how often and how drastically funding rates fluctuate:
- During periods of rapid price swings—such as during major news events—the spread between spot and future prices widens temporarily.
- These fluctuations cause corresponding jumps in financing costs for traders holding open positions.
- High volatility environments often see increased frequency of large positive or negative fundings as markets attempt self-correction mechanisms quickly respond to changing sentiments.
Such dynamics underscore why active monitoring becomes essential during turbulent times—they can dramatically alter profitability prospects for leveraged trades.
Regulatory Changes Affecting Funding Rates
Regulatory developments also play an influential role by shaping overall market sentiment—and consequently impacting funds' flow patterns:
- New rules around derivatives trading may impose restrictions that influence leverage limits,
- Changes requiring greater transparency could lead exchanges to modify calculation methods,
- Regulatory crackdowns might reduce overall trading activity affecting liquidity levels,
These factors indirectly impact how frequently and intensely funds change hands via differentials like those seen through varying funding rates across jurisdictions.
Risks Associated with Funding Rates
While beneficial for maintaining equilibrium under normal conditions,
extreme scenarios involving abnormal fundings pose risks such as:
- Market Destabilization: Excessively high positive/negative fundings may trigger mass liquidations if traders cannot sustain costs,
- Manipulation Potential: Some actors might attempt strategies exploiting predictable patterns within fee calculations,
- Trader Behavior Shifts: Unexpected changes could lead investors toward riskier behaviors like overleveraging before adverse shifts occur,
Therefore, prudent risk management practices—including setting stop-loss orders—is vital when operating under volatile conditions influenced by fluctuating fundings.
By grasping what determines your costs related to persistent holdings—and recognizing broader influences such as volatility trends—they become invaluable tools for informed decision-making within cryptocurrency derivatives markets.
Key Takeaways:
- The funding rate aligns perpetual contract pricing with underlying assets’ real-time values.
- Calculated regularly based on premium/discounts relative to spot prices.
- Impacts trader profitability directly through periodic payments.
- Fluctuates with market volatility & regulatory environment changes.
Staying aware of these dynamics enhances strategic planning—whether you're hedging risks or seeking arbitrage opportunities—in today’s fast-paced crypto landscape.
Semantic & LSI Keywords:
Perpetual swaps | Cryptocurrency derivatives | Futures contract pricing | Market liquidity | Trading fees | Leverage trading | Crypto regulation impacts | Volatility effects on derivatives


kai
2025-05-09 16:09
What is the funding rate in perpetual futures?
What is the Funding Rate in Perpetual Futures?
The funding rate is a fundamental concept in perpetual futures trading, especially within cryptocurrency markets. It acts as a mechanism to keep the price of perpetual contracts aligned with the underlying asset's spot price. Unlike traditional futures, which have fixed expiration dates, perpetual futures are designed to trade indefinitely. This unique feature necessitates a system—namely, the funding rate—to maintain market stability and liquidity over time.
In essence, the funding rate represents periodic payments exchanged between traders holding long and short positions based on prevailing market conditions. When used correctly, it helps prevent significant deviations between the futures contract price and the actual market value of the underlying asset.
How Does the Funding Rate Work?
The primary purpose of the funding rate is to balance supply and demand within perpetual futures markets. It operates on a regular schedule—often every 8 hours—where traders either pay or receive fees depending on their position type (long or short) and current market dynamics.
If traders collectively believe that prices will rise above spot prices, long positions tend to dominate. To prevent excessive divergence from real-world prices, exchanges implement a positive funding rate where longs pay shorts periodically. Conversely, if futures prices fall below spot prices due to bearish sentiment or other factors, negative funding rates may occur where shorts pay longs.
This payment flow incentivizes traders' behavior: high positive rates encourage some longs to close their positions or take profits while attracting more shorts; negative rates do just the opposite by encouraging longs to hold onto their positions despite unfavorable conditions.
Calculation of Funding Rates
Understanding how funding rates are calculated provides insight into their role in maintaining equilibrium:
- Basis Difference: The core component involves calculating the difference between current spot prices and futures contract prices.
- Interest Rate Component: Some models incorporate an interest component reflecting borrowing costs.
- Premium/Discount Adjustment: The calculation considers whether contracts are trading at a premium (above spot) or discount (below spot).
Most exchanges compute this rate every 8 hours using real-time data from both markets. The formula varies slightly across platforms but generally follows this pattern:
Funding Rate = (Futures Price - Spot Price) / Spot Price * Adjustment FactorWhere adjustments account for interest rates and other market factors specific to each exchange’s methodology.
Why Is The Funding Rate Important for Traders?
For traders engaged in perpetual futures trading, understanding how funding impacts profitability is crucial:
- Cost Management: A positive funding rate means holding long positions incurs periodic costs; negative rates mean short sellers face similar charges.
- Strategy Planning: Anticipating changes in fundings can influence entry/exit points—for example, avoiding entering new long positions when high positive rates are expected.
- Risk Control: Sudden spikes or drops in fundings often signal shifts in market sentiment or volatility; monitoring these can help mitigate potential losses.
Moreover, since these payments happen automatically at scheduled intervals through exchange mechanisms like wallet deductions or credits, they directly affect net gains/losses over time.
Impact of Market Volatility on Funding Rates
Market volatility significantly influences how often and how drastically funding rates fluctuate:
- During periods of rapid price swings—such as during major news events—the spread between spot and future prices widens temporarily.
- These fluctuations cause corresponding jumps in financing costs for traders holding open positions.
- High volatility environments often see increased frequency of large positive or negative fundings as markets attempt self-correction mechanisms quickly respond to changing sentiments.
Such dynamics underscore why active monitoring becomes essential during turbulent times—they can dramatically alter profitability prospects for leveraged trades.
Regulatory Changes Affecting Funding Rates
Regulatory developments also play an influential role by shaping overall market sentiment—and consequently impacting funds' flow patterns:
- New rules around derivatives trading may impose restrictions that influence leverage limits,
- Changes requiring greater transparency could lead exchanges to modify calculation methods,
- Regulatory crackdowns might reduce overall trading activity affecting liquidity levels,
These factors indirectly impact how frequently and intensely funds change hands via differentials like those seen through varying funding rates across jurisdictions.
Risks Associated with Funding Rates
While beneficial for maintaining equilibrium under normal conditions,
extreme scenarios involving abnormal fundings pose risks such as:
- Market Destabilization: Excessively high positive/negative fundings may trigger mass liquidations if traders cannot sustain costs,
- Manipulation Potential: Some actors might attempt strategies exploiting predictable patterns within fee calculations,
- Trader Behavior Shifts: Unexpected changes could lead investors toward riskier behaviors like overleveraging before adverse shifts occur,
Therefore, prudent risk management practices—including setting stop-loss orders—is vital when operating under volatile conditions influenced by fluctuating fundings.
By grasping what determines your costs related to persistent holdings—and recognizing broader influences such as volatility trends—they become invaluable tools for informed decision-making within cryptocurrency derivatives markets.
Key Takeaways:
- The funding rate aligns perpetual contract pricing with underlying assets’ real-time values.
- Calculated regularly based on premium/discounts relative to spot prices.
- Impacts trader profitability directly through periodic payments.
- Fluctuates with market volatility & regulatory environment changes.
Staying aware of these dynamics enhances strategic planning—whether you're hedging risks or seeking arbitrage opportunities—in today’s fast-paced crypto landscape.
Semantic & LSI Keywords:
Perpetual swaps | Cryptocurrency derivatives | Futures contract pricing | Market liquidity | Trading fees | Leverage trading | Crypto regulation impacts | Volatility effects on derivatives
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is the Difference Between a Hardware Wallet and a Software Wallet?
Understanding Cryptocurrency Storage Options
As cryptocurrencies become more mainstream, securing digital assets has become a top priority for investors and users alike. The two primary types of wallets used to store cryptocurrencies are hardware wallets and software wallets. Each offers distinct advantages and disadvantages, making it essential to understand their differences to choose the best option for your needs.
Hardware Wallets: Physical Devices for Secure Storage
A hardware wallet is a physical device designed specifically to securely store private keys offline. These devices often resemble USB drives or small electronic gadgets, making them portable and easy to carry. Because they keep private keys disconnected from internet-connected devices, hardware wallets significantly reduce exposure to online threats such as hacking or malware.
Key features of hardware wallets include enhanced security through offline storage, resistance against phishing attacks (since private keys are never exposed online), and user-friendly interfaces that simplify managing multiple cryptocurrencies. Popular models like Ledger Nano X, Trezor Model T, and KeepKey exemplify this category’s focus on security combined with ease of use.
Hardware wallets are particularly suitable for long-term investors or those holding substantial amounts of cryptocurrency because they prioritize safeguarding assets from cyber threats. However, they typically come at a higher cost compared to software options but provide peace of mind through robust physical protection.
Software Wallets: Digital Applications for Convenience
In contrast, software wallets are applications installed on computers or mobile devices that manage cryptocurrency holdings digitally. They can be desktop applications like Electrum, mobile apps such as Coinbase Wallet, or browser extensions like MetaMask. These wallets offer quick access to funds with just a few clicks or taps.
The main advantage of software wallets lies in their convenience—they’re easy to set up and use without requiring specialized technical knowledge. Users can access their crypto holdings anytime from any device connected to the internet—making them ideal for daily transactions or trading activities.
However, this accessibility comes with increased security risks; since private keys are stored on internet-connected devices—whether on desktops or smartphones—they’re more vulnerable to malware infections or phishing scams if proper precautions aren’t taken. Cost-wise, most software wallets are free or inexpensive but require diligent security practices by users.
Contextual Considerations: Security vs Accessibility
Choosing between hardware and software wallets depends largely on individual priorities regarding security versus convenience:
- Security Concerns: Hardware wallets excel here due to offline storage capabilities that make hacking attempts significantly more difficult.
- Ease of Use: Software solutions tend toward user-friendliness; beginners often find them easier initially.
- Frequency of Transactions: Active traders may prefer software options due to rapid access; long-term holders might favor hardware solutions for maximum safety.
- Asset Size: Larger holdings generally warrant higher-security measures provided by hardware devices; smaller amounts can be managed effectively via secure software setups.
Recent Trends in Cryptocurrency Storage Solutions
Over recent years, both types have seen technological advancements driven by increasing adoption:
- Hardware manufacturers now incorporate features like multi-signature support—requiring multiple approvals before transactions—and advanced encryption protocols enhancing overall security.
- Software wallet providers have integrated two-factor authentication (2FA), biometric verification (like fingerprint scans), and encrypted backups—all aimed at reducing vulnerabilities associated with online management.
- Regulatory bodies worldwide are beginning scrutinizing these storage methods more closely—potentially leading toward standardized security requirements across platforms.
- The competitive landscape continues evolving as startups introduce innovative solutions blending elements from both categories—for example, hybrid cold/hot wallet systems designed for optimal balance between safety and usability.
Risks & Best Practices When Choosing Crypto Storage Solutions
While each type offers benefits suited under different circumstances — understanding potential pitfalls is crucial:
For hardware wallets:
- Always purchase directly from reputable manufacturers
- Keep recovery seed phrases secure offline
- Avoid connecting the device on compromised computers
For software wallets:
- Use strong passwords
- Enable two-factor authentication where available
- Regularly update application firmware/software
Both options require diligent management; neglecting basic cybersecurity hygiene can compromise even the most secure systems.
How To Decide Which Wallet Fits Your Needs?
To determine whether you should opt for a hardware wallet versus a software wallet consider these factors:
- How much cryptocurrency do you plan on storing?
- Are you comfortable managing physical devices?
- Do you prioritize maximum security over ease of access?
- Will you need frequent transaction capabilities?
For large holdings intended as long-term investments—with minimal trading activity—a hardware wallet provides superior protection against thefts resulting from cyberattacks. Conversely—or additionally—for daily transactions involving smaller amounts—a well-secured software wallet may suffice if proper precautions are observed.
Emerging Developments in Cryptocurrency Security
The landscape continues evolving rapidly:
• Multi-signature technology allows multiple approvals before executing transactions—adding an extra layer of protection regardless of storage method.• Biometric authentication enhances user verification processes within both types but especially benefits mobile-based solutions.• Regulatory frameworks aim at standardizing best practices across providers—improving overall trustworthiness in crypto custody services.
Final Thoughts: Making an Informed Choice
Selecting between a hardware wallet and a software wallet ultimately hinges upon your specific needs related primarily to asset size, transaction frequency, technical comfort level—and how much risk you're willing—or able—to accept regarding potential cyber threats versus convenience demands.
By understanding these core differences—and staying informed about ongoing technological improvements—you can better safeguard your digital assets today while preparing effectively against future challenges in the dynamic world of cryptocurrencies.


JCUSER-WVMdslBw
2025-05-15 00:35
What is the difference between a hardware wallet and a software wallet?
What Is the Difference Between a Hardware Wallet and a Software Wallet?
Understanding Cryptocurrency Storage Options
As cryptocurrencies become more mainstream, securing digital assets has become a top priority for investors and users alike. The two primary types of wallets used to store cryptocurrencies are hardware wallets and software wallets. Each offers distinct advantages and disadvantages, making it essential to understand their differences to choose the best option for your needs.
Hardware Wallets: Physical Devices for Secure Storage
A hardware wallet is a physical device designed specifically to securely store private keys offline. These devices often resemble USB drives or small electronic gadgets, making them portable and easy to carry. Because they keep private keys disconnected from internet-connected devices, hardware wallets significantly reduce exposure to online threats such as hacking or malware.
Key features of hardware wallets include enhanced security through offline storage, resistance against phishing attacks (since private keys are never exposed online), and user-friendly interfaces that simplify managing multiple cryptocurrencies. Popular models like Ledger Nano X, Trezor Model T, and KeepKey exemplify this category’s focus on security combined with ease of use.
Hardware wallets are particularly suitable for long-term investors or those holding substantial amounts of cryptocurrency because they prioritize safeguarding assets from cyber threats. However, they typically come at a higher cost compared to software options but provide peace of mind through robust physical protection.
Software Wallets: Digital Applications for Convenience
In contrast, software wallets are applications installed on computers or mobile devices that manage cryptocurrency holdings digitally. They can be desktop applications like Electrum, mobile apps such as Coinbase Wallet, or browser extensions like MetaMask. These wallets offer quick access to funds with just a few clicks or taps.
The main advantage of software wallets lies in their convenience—they’re easy to set up and use without requiring specialized technical knowledge. Users can access their crypto holdings anytime from any device connected to the internet—making them ideal for daily transactions or trading activities.
However, this accessibility comes with increased security risks; since private keys are stored on internet-connected devices—whether on desktops or smartphones—they’re more vulnerable to malware infections or phishing scams if proper precautions aren’t taken. Cost-wise, most software wallets are free or inexpensive but require diligent security practices by users.
Contextual Considerations: Security vs Accessibility
Choosing between hardware and software wallets depends largely on individual priorities regarding security versus convenience:
- Security Concerns: Hardware wallets excel here due to offline storage capabilities that make hacking attempts significantly more difficult.
- Ease of Use: Software solutions tend toward user-friendliness; beginners often find them easier initially.
- Frequency of Transactions: Active traders may prefer software options due to rapid access; long-term holders might favor hardware solutions for maximum safety.
- Asset Size: Larger holdings generally warrant higher-security measures provided by hardware devices; smaller amounts can be managed effectively via secure software setups.
Recent Trends in Cryptocurrency Storage Solutions
Over recent years, both types have seen technological advancements driven by increasing adoption:
- Hardware manufacturers now incorporate features like multi-signature support—requiring multiple approvals before transactions—and advanced encryption protocols enhancing overall security.
- Software wallet providers have integrated two-factor authentication (2FA), biometric verification (like fingerprint scans), and encrypted backups—all aimed at reducing vulnerabilities associated with online management.
- Regulatory bodies worldwide are beginning scrutinizing these storage methods more closely—potentially leading toward standardized security requirements across platforms.
- The competitive landscape continues evolving as startups introduce innovative solutions blending elements from both categories—for example, hybrid cold/hot wallet systems designed for optimal balance between safety and usability.
Risks & Best Practices When Choosing Crypto Storage Solutions
While each type offers benefits suited under different circumstances — understanding potential pitfalls is crucial:
For hardware wallets:
- Always purchase directly from reputable manufacturers
- Keep recovery seed phrases secure offline
- Avoid connecting the device on compromised computers
For software wallets:
- Use strong passwords
- Enable two-factor authentication where available
- Regularly update application firmware/software
Both options require diligent management; neglecting basic cybersecurity hygiene can compromise even the most secure systems.
How To Decide Which Wallet Fits Your Needs?
To determine whether you should opt for a hardware wallet versus a software wallet consider these factors:
- How much cryptocurrency do you plan on storing?
- Are you comfortable managing physical devices?
- Do you prioritize maximum security over ease of access?
- Will you need frequent transaction capabilities?
For large holdings intended as long-term investments—with minimal trading activity—a hardware wallet provides superior protection against thefts resulting from cyberattacks. Conversely—or additionally—for daily transactions involving smaller amounts—a well-secured software wallet may suffice if proper precautions are observed.
Emerging Developments in Cryptocurrency Security
The landscape continues evolving rapidly:
• Multi-signature technology allows multiple approvals before executing transactions—adding an extra layer of protection regardless of storage method.• Biometric authentication enhances user verification processes within both types but especially benefits mobile-based solutions.• Regulatory frameworks aim at standardizing best practices across providers—improving overall trustworthiness in crypto custody services.
Final Thoughts: Making an Informed Choice
Selecting between a hardware wallet and a software wallet ultimately hinges upon your specific needs related primarily to asset size, transaction frequency, technical comfort level—and how much risk you're willing—or able—to accept regarding potential cyber threats versus convenience demands.
By understanding these core differences—and staying informed about ongoing technological improvements—you can better safeguard your digital assets today while preparing effectively against future challenges in the dynamic world of cryptocurrencies.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
📰 Leading financial institutions are developing proprietary blockchains to:
⚡️ Capture transaction fees
⚡️ Control their own economic model
⚡️ Reduce dependence on external networks
👉 The blockchain market in the banking industry is expected to reach $40.9 billion by 2029 with a CAGR of 39.4%! 📈
🔎 Read more: https://blog.jucoin.com/financial-companies-building-blockchains/
#JuCoin #JuCoinVietnam #JuCoinInsights #Blockchain #Web3 #Crypto


Lee Jucoin
2025-08-18 06:29
📣 JuCoin Insights | Why are financial giants building their own blockchains? 🌟
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How to Protect Yourself from Common Cryptocurrency Scams
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and digital transactions. However, with its rapid growth comes an increase in scams designed to exploit unsuspecting users. Understanding the most common types of cryptocurrency scams and adopting effective security practices are essential steps in safeguarding your assets and personal information.
Recognizing Common Cryptocurrency Scams
Being aware of prevalent scam tactics is the first line of defense. Here are some of the most widespread schemes:
Phishing Attacks
Phishing remains one of the most common methods scammers use to steal sensitive information. These attacks typically involve deceptive emails, messages, or websites that mimic legitimate exchanges or wallets. Victims may be tricked into revealing login credentials, private keys, or other confidential data. For example, a 2025 data breach at Coinbase exposed user details through sophisticated phishing campaigns targeting account holders.
Fake Exchanges and Wallets
Scammers often create counterfeit cryptocurrency platforms that look remarkably similar to real exchanges or wallets. They lure victims into depositing funds into these fake sites with promises of high returns or easy trading options. Once funds are transferred, scammers disappear with the money—leaving investors empty-handed.
Ponzi Schemes
Ponzi schemes promise high returns with little risk but rely on new investor funds to pay existing participants. The notorious BitConnect scheme (2016–2018) is a prime example where many investors suffered significant losses when the scheme collapsed.
ICO Scams
Initial Coin Offerings (ICOs) have been exploited by fraudsters creating fake projects that raise capital under false pretenses. In 2017, The DAO hack demonstrated how unregulated ICOs could lead to substantial financial losses for investors who trusted unverified whitepapers and promises.
Social Engineering Tactics
Scammers manipulate individuals psychologically—posing as trusted contacts like friends or family—to gain access to sensitive information or persuade victims to perform certain actions such as transferring funds or revealing passwords.
Malware and Ransomware Attacks
Cybercriminals deploy malicious software designed to infect devices and steal cryptocurrencies directly from wallets or encrypt files until ransom payments are made. A notable ransomware attack on a major exchange in 2023 underscored how cybersecurity vulnerabilities can threaten digital assets.
Recent Developments Enhancing Security Measures
The fight against cryptocurrency scams is ongoing, with regulatory bodies and technology developers implementing measures aimed at reducing risks:
Regulatory Efforts: Governments worldwide are establishing clearer guidelines for crypto activities; for instance, in 2024, the U.S SEC issued comprehensive ICO guidelines intended to curb fraudulent offerings.
Technological Innovations: Blockchain advancements such as multi-signature wallets require multiple approvals before transactions proceed—adding layers of security—and decentralized exchanges (DEXs) reduce reliance on centralized entities vulnerable to hacking.
Public Awareness Campaigns: Industry leaders have launched educational initiatives globally—for example, a 2025 campaign focused on educating users about scam recognition techniques—to empower individuals against fraud attempts.
Essential Strategies for Personal Protection Against Crypto Scams
Implementing robust security practices significantly reduces vulnerability:
Stay Educated: Continuously update your knowledge about emerging scams by following reputable sources within the crypto community.
Use Secure Wallets: Hardware wallets and multi-signature solutions provide enhanced protection compared to online hot wallets susceptible to hacking.
Verify Before Acting: Always double-check URLs before entering login details; beware of misspelled domains mimicking legitimate sites.
Exercise Caution With Investments: Be skeptical about offers promising unrealistically high returns; avoid unregulated platforms lacking transparency.
Enable Two-Factor Authentication (2FA): Adding an extra verification step helps prevent unauthorized access even if login credentials are compromised.
Keep Software Updated: Regularly update your operating system and applications—security patches close vulnerabilities exploited by malware.
Monitor Accounts Regularly: Frequently review transaction histories for suspicious activity; early detection can prevent further loss.
Choose Reputable Exchanges Only: Stick with well-established platforms known for strong security protocols rather than unknown entities promising quick profits.
Avoid Public Wi-Fi Usage During Transactions: Public networks pose risks; use secure connections when managing cryptocurrencies online.
Back Up Data Frequently: Maintain secure backups of wallet keys and important data offline—this ensures recovery options if devices are compromised by ransomware attacks.
Building Trust Through Due Diligence
Trustworthiness in cryptocurrency dealings hinges on thorough research: verify project backgrounds before investing in ICOs; scrutinize whitepapers; check regulatory compliance status; read reviews from credible sources within blockchain communities—all these steps help establish confidence while minimizing exposure risk.
By combining awareness of common scams with proactive security measures—including technological safeguards like hardware wallets—and maintaining vigilance through continuous education—you can significantly enhance your defenses against evolving threats within the crypto space. Staying informed not only protects your investments but also contributes positively toward building a safer digital financial environment overall.


JCUSER-IC8sJL1q
2025-05-22 17:33
How can I protect myself from common cryptocurrency scams?
How to Protect Yourself from Common Cryptocurrency Scams
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and digital transactions. However, with its rapid growth comes an increase in scams designed to exploit unsuspecting users. Understanding the most common types of cryptocurrency scams and adopting effective security practices are essential steps in safeguarding your assets and personal information.
Recognizing Common Cryptocurrency Scams
Being aware of prevalent scam tactics is the first line of defense. Here are some of the most widespread schemes:
Phishing Attacks
Phishing remains one of the most common methods scammers use to steal sensitive information. These attacks typically involve deceptive emails, messages, or websites that mimic legitimate exchanges or wallets. Victims may be tricked into revealing login credentials, private keys, or other confidential data. For example, a 2025 data breach at Coinbase exposed user details through sophisticated phishing campaigns targeting account holders.
Fake Exchanges and Wallets
Scammers often create counterfeit cryptocurrency platforms that look remarkably similar to real exchanges or wallets. They lure victims into depositing funds into these fake sites with promises of high returns or easy trading options. Once funds are transferred, scammers disappear with the money—leaving investors empty-handed.
Ponzi Schemes
Ponzi schemes promise high returns with little risk but rely on new investor funds to pay existing participants. The notorious BitConnect scheme (2016–2018) is a prime example where many investors suffered significant losses when the scheme collapsed.
ICO Scams
Initial Coin Offerings (ICOs) have been exploited by fraudsters creating fake projects that raise capital under false pretenses. In 2017, The DAO hack demonstrated how unregulated ICOs could lead to substantial financial losses for investors who trusted unverified whitepapers and promises.
Social Engineering Tactics
Scammers manipulate individuals psychologically—posing as trusted contacts like friends or family—to gain access to sensitive information or persuade victims to perform certain actions such as transferring funds or revealing passwords.
Malware and Ransomware Attacks
Cybercriminals deploy malicious software designed to infect devices and steal cryptocurrencies directly from wallets or encrypt files until ransom payments are made. A notable ransomware attack on a major exchange in 2023 underscored how cybersecurity vulnerabilities can threaten digital assets.
Recent Developments Enhancing Security Measures
The fight against cryptocurrency scams is ongoing, with regulatory bodies and technology developers implementing measures aimed at reducing risks:
Regulatory Efforts: Governments worldwide are establishing clearer guidelines for crypto activities; for instance, in 2024, the U.S SEC issued comprehensive ICO guidelines intended to curb fraudulent offerings.
Technological Innovations: Blockchain advancements such as multi-signature wallets require multiple approvals before transactions proceed—adding layers of security—and decentralized exchanges (DEXs) reduce reliance on centralized entities vulnerable to hacking.
Public Awareness Campaigns: Industry leaders have launched educational initiatives globally—for example, a 2025 campaign focused on educating users about scam recognition techniques—to empower individuals against fraud attempts.
Essential Strategies for Personal Protection Against Crypto Scams
Implementing robust security practices significantly reduces vulnerability:
Stay Educated: Continuously update your knowledge about emerging scams by following reputable sources within the crypto community.
Use Secure Wallets: Hardware wallets and multi-signature solutions provide enhanced protection compared to online hot wallets susceptible to hacking.
Verify Before Acting: Always double-check URLs before entering login details; beware of misspelled domains mimicking legitimate sites.
Exercise Caution With Investments: Be skeptical about offers promising unrealistically high returns; avoid unregulated platforms lacking transparency.
Enable Two-Factor Authentication (2FA): Adding an extra verification step helps prevent unauthorized access even if login credentials are compromised.
Keep Software Updated: Regularly update your operating system and applications—security patches close vulnerabilities exploited by malware.
Monitor Accounts Regularly: Frequently review transaction histories for suspicious activity; early detection can prevent further loss.
Choose Reputable Exchanges Only: Stick with well-established platforms known for strong security protocols rather than unknown entities promising quick profits.
Avoid Public Wi-Fi Usage During Transactions: Public networks pose risks; use secure connections when managing cryptocurrencies online.
Back Up Data Frequently: Maintain secure backups of wallet keys and important data offline—this ensures recovery options if devices are compromised by ransomware attacks.
Building Trust Through Due Diligence
Trustworthiness in cryptocurrency dealings hinges on thorough research: verify project backgrounds before investing in ICOs; scrutinize whitepapers; check regulatory compliance status; read reviews from credible sources within blockchain communities—all these steps help establish confidence while minimizing exposure risk.
By combining awareness of common scams with proactive security measures—including technological safeguards like hardware wallets—and maintaining vigilance through continuous education—you can significantly enhance your defenses against evolving threats within the crypto space. Staying informed not only protects your investments but also contributes positively toward building a safer digital financial environment overall.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Start your new week full of energy with the journey of exploring crypto, trading smart and building the future of Web3 today with #JuCoin! 🌱✨
👉 Experience and Register JuCoin now: https://bit.ly/3BVxlZ2
#JuCoin #JucoinVietnam #Crypto #Web3 #Blockchain #Trading


Lee Jucoin
2025-08-18 06:30
🌟 GM GM! New Week, New Opportunities with #JuCoin 🚀
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
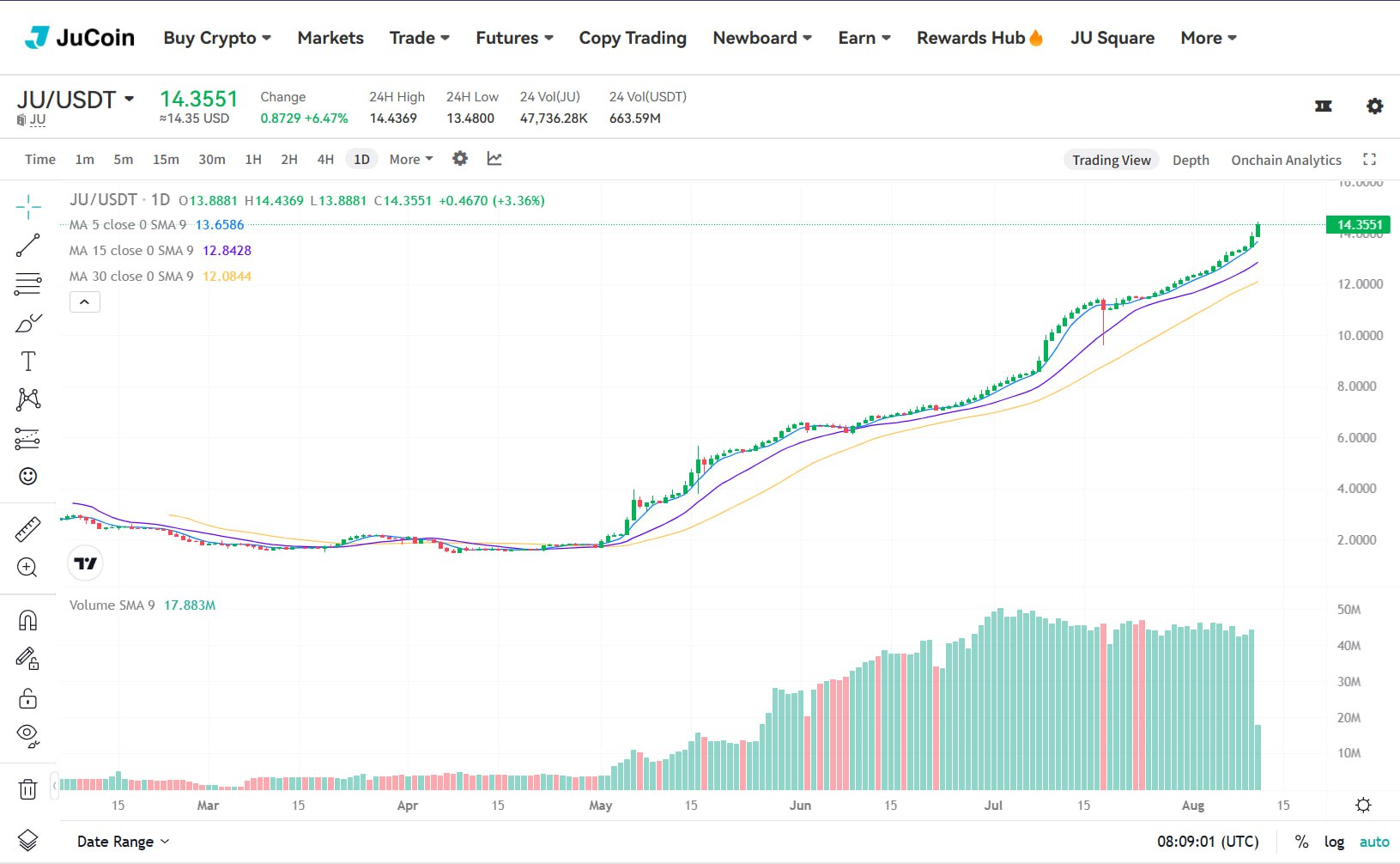
+140x ROI depuis le lancement — du jamais vu dans le marché actuel. Merci à tous les builders, holders & believers Le sommet ? Ce n’est que le départ. Jusqu’au 12 août, 19h00 (UTC+8)


Carmelita
2025-08-11 21:33
$JU explose un nouveau record : 14 $ franchis !
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
The blockchain space is fragmented into hundreds of isolated networks - Bitcoin's security, Ethereum's smart contracts, faster chains for low costs. This "silo problem" limits DeFi potential and user experience. Here's why cross-chain connectivity is the future:
🔗 What Is Interoperability:
-
Enables different blockchains to communicate and share data
Allows seamless asset transfers between networks
Creates a unified decentralized ecosystem like the early internet
⚙️ How It Works:
-
Cross-Chain Bridges: Lock assets on one chain, mint wrapped versions on another (like WBTC)
IBC Protocols: Direct message passing between compatible blockchains (Cosmos hub-and-spoke model)
Atomic Swaps: Peer-to-peer exchanges without centralized intermediaries
Oracles: Connect blockchains to external data and other networks
💡 Benefits of Connected Future:
-
Massive liquidity improvement and capital efficiency
Access wider range of services regardless of asset origin
Developers can leverage strengths of multiple chains
Simplified user experience - one wallet, seamless access
⚠️ Current Challenges:
-
Security vulnerabilities (billions lost in bridge exploits)
Complex technical specifications across different chains
Lack of standardized protocols
Single points of failure in cross-chain solutions
🎯 Key Impact: Without interoperability, blockchains remain "walled gardens" limiting innovation. Future solutions like native IBC and atomic swaps promise more secure connectivity, unlocking new use cases and creating the seamless Web3 experience users expect.
The race is on to solve the interoperability puzzle - whoever cracks it will unlock the true potential of a connected blockchain ecosystem.
Read the full deep-dive analysis: 👇 https://blog.jucoin.com/blockchain-interoperability-why-it-matters/
#Blockchain #Interoperability #CrossChain #DeFi #Web3



JU Blog
2025-08-06 10:43
🌐 Blockchain Interoperability: Breaking Down the Silos!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
InterLink introduces an innovative dual-token architecture that separates compliance from participation, creating a sustainable ecosystem where institutions and individuals thrive together. Here's the breakthrough approach:
🏛️ $ITL Token (Compliance Layer):
-
1 billion total supply for institutions and ecosystem funds
Staking required for "Human Layer" access rights
Reputation-based validation prevents malicious nodes
Institutional holders earn transaction fee shares
👥 $ITLG Token (Incentive Layer):
-
10 billion supply: 80% for human nodes, 20% for governance
Earned through facial recognition verification + referrals
Daily mining rewards based on activity and contributions
Powers DAO governance with 1 token = 1 vote
🚀 Key Innovation - Human Node Validation:
-
Facial recognition prevents bot farming
Social referral system ensures authentic users
Activity scoring rewards genuine participation
Avoids PoW/PoS centralization risks
⚖️ DAO Governance Features:
-
Linear voting prevents whale domination
Smart contract auto-execution
Full on-chain transparency
Community-driven protocol evolution
🌍 Real-World Applications:
-
Humanitarian Aid: Direct peer-to-peer payments to disaster victims
Financial Inclusion: Digital payments for unbanked populations
Data Monetization: Secure data licensing for $ITLG rewards
Social Governance: Community polls and collaborative projects
📈 2025 Roadmap:
-
50+ country expansion with regional validator nodes
Cross-chain bridges to Ethereum, Avalanche, Cosmos
Human Layer SDK for developers
InterLink Rating (IR) system for enhanced autonomy
💡 Why It Matters: This dual-token approach solves the age-old problem of balancing institutional compliance with genuine user participation. While institutions provide stability through $ITL staking, real users drive network vitality through $ITLG incentives - creating the first truly human-centered DeFi ecosystem.
The future of crypto isn't just about code - it's about people. InterLink proves that sustainable tokenomics must center on human validation and authentic participation.
Read the complete tokenomics breakdown: 👇 https://blog.jucoin.com/interlink-dual-tokenomics/
#InterLink #DualToken #DeFi #DAO #Tokenomics



JU Blog
2025-08-06 10:45
🔗 InterLink's Revolutionary Dual-Token Model: Human-Centered DeFi!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🔐 Les banques ne pourront plus couper l’accès aux clients légitimes, y compris dans les **actifs numériques**.
#CryptoPolicy #DigitalAssets #Web3




Carmelita
2025-08-07 20:18
🇺🇸 Trump signe un décret interdisant le “debanking politique”.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Are 3Commas Pricing Tiers?
Understanding the different pricing options available on 3Commas is essential for traders looking to optimize their cryptocurrency trading strategies. As a platform that caters to both beginners and seasoned professionals, 3Commas offers a tiered subscription model designed to meet varying needs and budgets. This article provides an in-depth overview of these tiers, their features, target audiences, and recent platform updates.
Overview of 3Commas as a Cryptocurrency Trading Platform
Founded in 2017 by Yuriy Serdyuk and Oleksandr Lutskevych, 3Commas has established itself as a leading tool in the crypto trading space. Its user-friendly interface combined with powerful automation tools has attracted traders worldwide. The platform supports multiple exchanges such as Binance, Coinbase Pro, Kraken, and others—allowing users to manage diverse portfolios seamlessly.
Key features include automated trading bots that execute trades based on predefined strategies, backtesting tools for strategy validation before live deployment, and social trading functionalities where users can follow or copy successful traders. These capabilities make it suitable for both novices exploring automated trading and professional traders seeking advanced algorithmic solutions.
The Three Main Pricing Tiers
As of now, 3Commas offers three primary subscription plans: Free, Premium (at $34/month), and Pro (at $99/month). Each tier is structured to provide increasing levels of access to features aligned with trader experience levels.
Free Plan: Entry-Level Access
The free plan serves as an excellent starting point for newcomers interested in exploring automated crypto trading without financial commitment. It includes basic functionalities such as limited access to simple trading bots—often one or two—and some backtesting capabilities. However, these are restricted compared to paid plans; users can only trade on select pairs with limited customization options.
This tier is ideal for those who want hands-on experience with minimal risk or cost before deciding whether more advanced tools are necessary. It also allows new traders to familiarize themselves with the platform’s interface while testing initial strategies.
Premium Plan: Intermediate Features at $34/Month
Designed for active traders seeking more control over their automation strategies without breaking the bank, the Premium plan unlocks full backtesting capabilities—a crucial feature for refining algorithms before deploying them live. Users gain access to a broader range of trading pairs and customizable bot settings that enable more sophisticated trade execution.
Priority customer support is another benefit here; this ensures quicker assistance when technical issues arise or strategic questions need addressing. Overall, this plan strikes a balance between affordability and functionality suitable for intermediate-level traders aiming to enhance their performance through automation.
Pro Plan: Advanced Tools at $99/Month
The most comprehensive offering from 3Commas targets professional or highly active crypto traders who require cutting-edge features. The Pro plan includes customizable algorithms powered by real-time data feeds—providing more accurate market insights—and dedicated account management services tailored toward high-frequency or large-volume trades.
Exclusive content such as premium signals and detailed market analysis further empowers users making complex decisions quickly within volatile markets. This tier demands higher investment but delivers tools suited for those operating at an institutional level or managing significant portfolios requiring personalized support.
Recent Platform Developments Enhancing User Experience
In recent months, 3Commas has focused heavily on expanding its ecosystem through several key updates:
Integration With Additional Exchanges: By partnering with new platforms like Bitfinex and Huobi Global recently integrated into its system—users now have access to even wider liquidity pools.
Enhanced Security Measures: Recognizing the importance of safeguarding user assets amid rising cyber threats in crypto space—the platform introduced two-factor authentication improvements along with stronger encryption protocols.
Community Engagement Initiatives: Active communication channels via social media forums allow users feedback-driven development cycles; this helps tailor future updates based on actual trader needs rather than assumptions alone.
These enhancements demonstrate how committed 3Commas remains towards providing secure yet innovative solutions tailored toward evolving market demands.
Potential Risks Associated With Subscription Tiers
While flexible pricing makes it accessible across various trader profiles—including beginners—the reliance on paid plans introduces certain risks:
Cost Considerations: For individual hobbyists or small-scale investors operating under tight budgets—especially those considering the Pro plan—the monthly expense might be prohibitive relative to expected gains.
Dependence On Technology & Data Feeds: Automated systems rely heavily on stable internet connections plus accurate real-time data feeds; any disruption could impact trade execution adversely.
Regulatory Environment Changes: As governments worldwide tighten regulations around cryptocurrencies—and some exchanges face restrictions—the integration capabilities offered by platforms like 3Commas could be affected unexpectedly.
Being aware of these factors helps ensure informed decision-making when choosing an appropriate subscription level aligned with personal risk tolerance and operational requirements.
Who Should Choose Which Tier?
Selecting the right plan depends largely on your experience level:
- Beginners should start with the free version—to learn how automated bots work without financial exposure—and upgrade later if needed.
- Intermediate traders aiming for better customization should consider upgrading to Premium ($34/month) once comfortable managing multiple pairs simultaneously.
- Professional operators executing high-frequency trades—or managing large portfolios—are best served by investing in Pro ($99/month), which offers advanced algorithms coupled with dedicated support services.
Final Thoughts: Making Informed Choices Based On Your Trading Goals
Understanding what each pricing tier offers enables you not only maximize your investment but also align your choice closely with your skill set — whether you're just starting out or already operating at an expert level within cryptocurrency markets.
By staying updated about recent developments like exchange integrations or security upgrades—as well as being mindful of potential risks—you can leverage platforms like 3Commas effectively while minimizing vulnerabilities associated with reliance solely on technology-driven solutions.
Keywords: cryptocurrency trading platforms | automated crypto bots | crypto exchange integration | backtesting tools | social trading | crypto portfolio management | beginner vs professional trader | subscription plans comparison


JCUSER-IC8sJL1q
2025-05-26 14:37
What are 3Commas pricing tiers?
What Are 3Commas Pricing Tiers?
Understanding the different pricing options available on 3Commas is essential for traders looking to optimize their cryptocurrency trading strategies. As a platform that caters to both beginners and seasoned professionals, 3Commas offers a tiered subscription model designed to meet varying needs and budgets. This article provides an in-depth overview of these tiers, their features, target audiences, and recent platform updates.
Overview of 3Commas as a Cryptocurrency Trading Platform
Founded in 2017 by Yuriy Serdyuk and Oleksandr Lutskevych, 3Commas has established itself as a leading tool in the crypto trading space. Its user-friendly interface combined with powerful automation tools has attracted traders worldwide. The platform supports multiple exchanges such as Binance, Coinbase Pro, Kraken, and others—allowing users to manage diverse portfolios seamlessly.
Key features include automated trading bots that execute trades based on predefined strategies, backtesting tools for strategy validation before live deployment, and social trading functionalities where users can follow or copy successful traders. These capabilities make it suitable for both novices exploring automated trading and professional traders seeking advanced algorithmic solutions.
The Three Main Pricing Tiers
As of now, 3Commas offers three primary subscription plans: Free, Premium (at $34/month), and Pro (at $99/month). Each tier is structured to provide increasing levels of access to features aligned with trader experience levels.
Free Plan: Entry-Level Access
The free plan serves as an excellent starting point for newcomers interested in exploring automated crypto trading without financial commitment. It includes basic functionalities such as limited access to simple trading bots—often one or two—and some backtesting capabilities. However, these are restricted compared to paid plans; users can only trade on select pairs with limited customization options.
This tier is ideal for those who want hands-on experience with minimal risk or cost before deciding whether more advanced tools are necessary. It also allows new traders to familiarize themselves with the platform’s interface while testing initial strategies.
Premium Plan: Intermediate Features at $34/Month
Designed for active traders seeking more control over their automation strategies without breaking the bank, the Premium plan unlocks full backtesting capabilities—a crucial feature for refining algorithms before deploying them live. Users gain access to a broader range of trading pairs and customizable bot settings that enable more sophisticated trade execution.
Priority customer support is another benefit here; this ensures quicker assistance when technical issues arise or strategic questions need addressing. Overall, this plan strikes a balance between affordability and functionality suitable for intermediate-level traders aiming to enhance their performance through automation.
Pro Plan: Advanced Tools at $99/Month
The most comprehensive offering from 3Commas targets professional or highly active crypto traders who require cutting-edge features. The Pro plan includes customizable algorithms powered by real-time data feeds—providing more accurate market insights—and dedicated account management services tailored toward high-frequency or large-volume trades.
Exclusive content such as premium signals and detailed market analysis further empowers users making complex decisions quickly within volatile markets. This tier demands higher investment but delivers tools suited for those operating at an institutional level or managing significant portfolios requiring personalized support.
Recent Platform Developments Enhancing User Experience
In recent months, 3Commas has focused heavily on expanding its ecosystem through several key updates:
Integration With Additional Exchanges: By partnering with new platforms like Bitfinex and Huobi Global recently integrated into its system—users now have access to even wider liquidity pools.
Enhanced Security Measures: Recognizing the importance of safeguarding user assets amid rising cyber threats in crypto space—the platform introduced two-factor authentication improvements along with stronger encryption protocols.
Community Engagement Initiatives: Active communication channels via social media forums allow users feedback-driven development cycles; this helps tailor future updates based on actual trader needs rather than assumptions alone.
These enhancements demonstrate how committed 3Commas remains towards providing secure yet innovative solutions tailored toward evolving market demands.
Potential Risks Associated With Subscription Tiers
While flexible pricing makes it accessible across various trader profiles—including beginners—the reliance on paid plans introduces certain risks:
Cost Considerations: For individual hobbyists or small-scale investors operating under tight budgets—especially those considering the Pro plan—the monthly expense might be prohibitive relative to expected gains.
Dependence On Technology & Data Feeds: Automated systems rely heavily on stable internet connections plus accurate real-time data feeds; any disruption could impact trade execution adversely.
Regulatory Environment Changes: As governments worldwide tighten regulations around cryptocurrencies—and some exchanges face restrictions—the integration capabilities offered by platforms like 3Commas could be affected unexpectedly.
Being aware of these factors helps ensure informed decision-making when choosing an appropriate subscription level aligned with personal risk tolerance and operational requirements.
Who Should Choose Which Tier?
Selecting the right plan depends largely on your experience level:
- Beginners should start with the free version—to learn how automated bots work without financial exposure—and upgrade later if needed.
- Intermediate traders aiming for better customization should consider upgrading to Premium ($34/month) once comfortable managing multiple pairs simultaneously.
- Professional operators executing high-frequency trades—or managing large portfolios—are best served by investing in Pro ($99/month), which offers advanced algorithms coupled with dedicated support services.
Final Thoughts: Making Informed Choices Based On Your Trading Goals
Understanding what each pricing tier offers enables you not only maximize your investment but also align your choice closely with your skill set — whether you're just starting out or already operating at an expert level within cryptocurrency markets.
By staying updated about recent developments like exchange integrations or security upgrades—as well as being mindful of potential risks—you can leverage platforms like 3Commas effectively while minimizing vulnerabilities associated with reliance solely on technology-driven solutions.
Keywords: cryptocurrency trading platforms | automated crypto bots | crypto exchange integration | backtesting tools | social trading | crypto portfolio management | beginner vs professional trader | subscription plans comparison
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Best Practices for Ensuring Safe Use of Decentralized Applications (dApps)
Decentralized applications, or dApps, are transforming how we interact with digital services by leveraging blockchain technology. They promise transparency, security, and community-driven control but also come with unique risks that users and developers must navigate carefully. Understanding the best practices for safe use is essential to protect assets, maintain trust, and foster sustainable growth in this innovative space.
Understanding Decentralized Applications and Their Security Challenges
Decentralized applications operate on blockchain networks using smart contracts—self-executing code that automates transactions based on predefined rules. Unlike traditional apps hosted on centralized servers, dApps distribute data across multiple nodes worldwide. This architecture reduces single points of failure but introduces specific vulnerabilities such as smart contract bugs, phishing scams, and reentrancy attacks.
Smart contract vulnerabilities are among the most critical risks because once deployed without proper auditing, they can be exploited to drain funds or manipulate outcomes. Phishing remains a common threat where malicious actors impersonate legitimate dApps or wallets to steal private keys or credentials. Reentrancy attacks exploit recursive calls within smart contracts to drain assets unexpectedly.
Given these challenges, adopting comprehensive safety measures is vital for both users engaging with dApps and developers building them.
Conduct Regular Smart Contract Audits
One of the foundational best practices is conducting thorough audits of smart contracts before deployment. These audits involve analyzing code for vulnerabilities using specialized tools like Etherscan’s security features or open-source frameworks such as OpenZeppelin’s security libraries. Engaging reputable cybersecurity firms specializing in blockchain ensures an independent review that can identify hidden flaws not apparent during initial development.
Regular audits should also be part of ongoing maintenance—especially after updates or feature additions—to ensure new code doesn’t introduce vulnerabilities. Transparent audit reports build user confidence by demonstrating a commitment to security standards.
Educate Users About Risks and Safe Practices
User education plays a crucial role in maintaining safety within the decentralized ecosystem. Many incidents stem from simple mistakes like falling victim to phishing scams or mishandling private keys. Providing clear guidance on recognizing authentic dApp links versus malicious sites helps prevent credential theft.
Encouraging users to verify URLs carefully before connecting wallets minimizes exposure to impersonation attempts. Additionally, promoting awareness about common attack vectors—such as social engineering tactics—empowers users to make informed decisions when interacting with decentralized platforms.
Educational resources should include tutorials on setting up hardware wallets securely (e.g., Ledger or Trezor), understanding transaction confirmations, and avoiding sharing sensitive information online.
Implement Multi-Signature Wallets for Enhanced Security
Multi-signature (multi-sig) wallets require multiple private keys before executing transactions—a significant upgrade over single-key setups prone to theft if compromised. For organizations managing large funds via dApps or communities participating in governance tokens, multi-sig arrangements add an extra layer of protection against unauthorized access.
This approach ensures no single individual can unilaterally move assets without consensus from designated signatories—a critical safeguard against internal threats and external hacking attempts alike.
Keep Software Up-to-Date With Latest Security Patches
The rapidly evolving nature of blockchain technology means software updates often include important security patches addressing newly discovered vulnerabilities. Users should regularly update their wallet applications—including browser extensions—and ensure their operating systems are current with latest patches from vendors like Apple or Microsoft.
Developers must also prioritize deploying updates promptly after fixing bugs identified through audits or bug bounty programs; delaying these updates leaves systems exposed unnecessarily.
Protect Against Phishing Attacks Through Vigilance
Phishing remains one of the most prevalent threats targeting dApp users due to its simplicity yet high impact potential when successful. Attackers craft convincing fake websites mimicking legitimate platforms aiming to steal login credentials or seed phrases used for wallet recovery.
To mitigate this risk:
- Always verify website URLs carefully.
- Avoid clicking links received via unsolicited emails.
- Use bookmarks for trusted sites.
- Enable two-factor authentication where possible.
Educating your community about these precautions significantly reduces susceptibility toward phishing schemes.
Backup Wallet Data Securely
In case of hardware failure thefts—or accidental loss—having secure backups ensures asset recovery without catastrophic loss. Hardware wallets like Ledger Nano S/Trezor provide seed phrases that allow restoring access across devices if needed.
Best practices include:
- Storing backup seed phrases offline in secure locations.
- Using encrypted storage solutions.
- Avoiding cloud-based backups susceptible to hacking.
Regularly updating backup copies guarantees they remain valid even after software changes over time.
Engage With Community & Participate in Bug Bounty Programs
Active engagement within developer communities enhances overall ecosystem safety by fostering transparency around potential issues early on rather than waiting until exploits occur publicly.
Many projects now run bug bounty programs incentivizing white-hat hackers worldwide who discover vulnerabilities responsibly before malicious actors do — leading directly toward more resilient systems.
Participating actively helps you stay informed about emerging threats while contributing positively toward collective cybersecurity efforts.
Recent Developments Improving Safety Standards
The landscape surrounding decentralized application safety continues improving thanks largely due to recent innovations:
Regulatory Clarity: Governments increasingly clarify legal frameworks around cryptocurrencies which encourages responsible development practices while reducing uncertainty that could lead developers astray into risky behaviors.
Advanced Security Tools: Companies such as Chainalysis offer sophisticated analytics solutions capable of monitoring illicit activities—including money laundering—in real-time across blockchain networks enhancing compliance efforts globally.
Bug Bounty Initiatives: The proliferation of bug bounty programs incentivizes proactive vulnerability discovery; some projects have rewarded millions USD worth of bounties leading directly toward safer deployments.
Enhanced Risk Management Strategies: DeFi protocols now incorporate collateralization safeguards alongside insurance options designed specifically against flash loan exploits—a common attack vector recently gaining prominence.
Risks That Still Loom Large
Despite progress made through best practices and technological advancements several risks persist:
- User errors resulting in lost funds remain prevalent if individuals neglect recommended precautions such as backups & verification steps
- Regulatory crackdowns could impose restrictions hindering innovation if compliance isn’t prioritized
- Major breaches could tarnish entire ecosystems’ reputation causing widespread distrust among new adopters
Staying vigilant by continuously applying updated best practices is essential for mitigating these dangers effectively.
Staying Ahead: The Path Forward
As decentralization continues expanding into mainstream finance (DeFi), gaming NFTs, DAOs—and beyond—the importance placed upon robust security measures grows exponentially.. Developers must prioritize transparent auditing processes; educate their communities proactively; implement multi-signature controls; keep all software current; monitor emerging threats vigilantly—and participate actively within ecosystems through bug bounty initiatives.
By doing so not only protects individual assets but also fosters trust necessary for broader adoption—all while contributing meaningfully towards a safer decentralized future.
This article aims at providing clarity around practical steps everyone involved with dApps can take today.


JCUSER-WVMdslBw
2025-05-23 01:42
What best practices ensure safe use of decentralized applications?
Best Practices for Ensuring Safe Use of Decentralized Applications (dApps)
Decentralized applications, or dApps, are transforming how we interact with digital services by leveraging blockchain technology. They promise transparency, security, and community-driven control but also come with unique risks that users and developers must navigate carefully. Understanding the best practices for safe use is essential to protect assets, maintain trust, and foster sustainable growth in this innovative space.
Understanding Decentralized Applications and Their Security Challenges
Decentralized applications operate on blockchain networks using smart contracts—self-executing code that automates transactions based on predefined rules. Unlike traditional apps hosted on centralized servers, dApps distribute data across multiple nodes worldwide. This architecture reduces single points of failure but introduces specific vulnerabilities such as smart contract bugs, phishing scams, and reentrancy attacks.
Smart contract vulnerabilities are among the most critical risks because once deployed without proper auditing, they can be exploited to drain funds or manipulate outcomes. Phishing remains a common threat where malicious actors impersonate legitimate dApps or wallets to steal private keys or credentials. Reentrancy attacks exploit recursive calls within smart contracts to drain assets unexpectedly.
Given these challenges, adopting comprehensive safety measures is vital for both users engaging with dApps and developers building them.
Conduct Regular Smart Contract Audits
One of the foundational best practices is conducting thorough audits of smart contracts before deployment. These audits involve analyzing code for vulnerabilities using specialized tools like Etherscan’s security features or open-source frameworks such as OpenZeppelin’s security libraries. Engaging reputable cybersecurity firms specializing in blockchain ensures an independent review that can identify hidden flaws not apparent during initial development.
Regular audits should also be part of ongoing maintenance—especially after updates or feature additions—to ensure new code doesn’t introduce vulnerabilities. Transparent audit reports build user confidence by demonstrating a commitment to security standards.
Educate Users About Risks and Safe Practices
User education plays a crucial role in maintaining safety within the decentralized ecosystem. Many incidents stem from simple mistakes like falling victim to phishing scams or mishandling private keys. Providing clear guidance on recognizing authentic dApp links versus malicious sites helps prevent credential theft.
Encouraging users to verify URLs carefully before connecting wallets minimizes exposure to impersonation attempts. Additionally, promoting awareness about common attack vectors—such as social engineering tactics—empowers users to make informed decisions when interacting with decentralized platforms.
Educational resources should include tutorials on setting up hardware wallets securely (e.g., Ledger or Trezor), understanding transaction confirmations, and avoiding sharing sensitive information online.
Implement Multi-Signature Wallets for Enhanced Security
Multi-signature (multi-sig) wallets require multiple private keys before executing transactions—a significant upgrade over single-key setups prone to theft if compromised. For organizations managing large funds via dApps or communities participating in governance tokens, multi-sig arrangements add an extra layer of protection against unauthorized access.
This approach ensures no single individual can unilaterally move assets without consensus from designated signatories—a critical safeguard against internal threats and external hacking attempts alike.
Keep Software Up-to-Date With Latest Security Patches
The rapidly evolving nature of blockchain technology means software updates often include important security patches addressing newly discovered vulnerabilities. Users should regularly update their wallet applications—including browser extensions—and ensure their operating systems are current with latest patches from vendors like Apple or Microsoft.
Developers must also prioritize deploying updates promptly after fixing bugs identified through audits or bug bounty programs; delaying these updates leaves systems exposed unnecessarily.
Protect Against Phishing Attacks Through Vigilance
Phishing remains one of the most prevalent threats targeting dApp users due to its simplicity yet high impact potential when successful. Attackers craft convincing fake websites mimicking legitimate platforms aiming to steal login credentials or seed phrases used for wallet recovery.
To mitigate this risk:
- Always verify website URLs carefully.
- Avoid clicking links received via unsolicited emails.
- Use bookmarks for trusted sites.
- Enable two-factor authentication where possible.
Educating your community about these precautions significantly reduces susceptibility toward phishing schemes.
Backup Wallet Data Securely
In case of hardware failure thefts—or accidental loss—having secure backups ensures asset recovery without catastrophic loss. Hardware wallets like Ledger Nano S/Trezor provide seed phrases that allow restoring access across devices if needed.
Best practices include:
- Storing backup seed phrases offline in secure locations.
- Using encrypted storage solutions.
- Avoiding cloud-based backups susceptible to hacking.
Regularly updating backup copies guarantees they remain valid even after software changes over time.
Engage With Community & Participate in Bug Bounty Programs
Active engagement within developer communities enhances overall ecosystem safety by fostering transparency around potential issues early on rather than waiting until exploits occur publicly.
Many projects now run bug bounty programs incentivizing white-hat hackers worldwide who discover vulnerabilities responsibly before malicious actors do — leading directly toward more resilient systems.
Participating actively helps you stay informed about emerging threats while contributing positively toward collective cybersecurity efforts.
Recent Developments Improving Safety Standards
The landscape surrounding decentralized application safety continues improving thanks largely due to recent innovations:
Regulatory Clarity: Governments increasingly clarify legal frameworks around cryptocurrencies which encourages responsible development practices while reducing uncertainty that could lead developers astray into risky behaviors.
Advanced Security Tools: Companies such as Chainalysis offer sophisticated analytics solutions capable of monitoring illicit activities—including money laundering—in real-time across blockchain networks enhancing compliance efforts globally.
Bug Bounty Initiatives: The proliferation of bug bounty programs incentivizes proactive vulnerability discovery; some projects have rewarded millions USD worth of bounties leading directly toward safer deployments.
Enhanced Risk Management Strategies: DeFi protocols now incorporate collateralization safeguards alongside insurance options designed specifically against flash loan exploits—a common attack vector recently gaining prominence.
Risks That Still Loom Large
Despite progress made through best practices and technological advancements several risks persist:
- User errors resulting in lost funds remain prevalent if individuals neglect recommended precautions such as backups & verification steps
- Regulatory crackdowns could impose restrictions hindering innovation if compliance isn’t prioritized
- Major breaches could tarnish entire ecosystems’ reputation causing widespread distrust among new adopters
Staying vigilant by continuously applying updated best practices is essential for mitigating these dangers effectively.
Staying Ahead: The Path Forward
As decentralization continues expanding into mainstream finance (DeFi), gaming NFTs, DAOs—and beyond—the importance placed upon robust security measures grows exponentially.. Developers must prioritize transparent auditing processes; educate their communities proactively; implement multi-signature controls; keep all software current; monitor emerging threats vigilantly—and participate actively within ecosystems through bug bounty initiatives.
By doing so not only protects individual assets but also fosters trust necessary for broader adoption—all while contributing meaningfully towards a safer decentralized future.
This article aims at providing clarity around practical steps everyone involved with dApps can take today.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🔓 With the new integration, 30% of #CORNCONSENSUS users' deposits will be automatically transferred to #JuTrust's insurance pool. #JuTrust records deposit/withdrawal transactions → is a transparent & automatic claim processing facility.⚡️
👉 Details: https://support.jucoin.blog/hc/en-001/articles/49844898901401
#JuCoin #JuCoinVietnam #JuTrust #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-18 06:28
📣 CORN CONSENSUS x JuTrust Insurance Vault! 🚀
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Proof-of-Stake (PoS) Explained: A Clear Guide for Beginners and Enthusiasts
Understanding Proof-of-Stake (PoS) is essential for anyone interested in blockchain technology, cryptocurrencies, or the future of decentralized networks. As an alternative to the traditional Proof-of-Work (PoW), PoS offers a more energy-efficient and scalable way to secure blockchain networks. This article breaks down what PoS is, how it works, its advantages and challenges, recent developments, and what it means for the future of digital currencies.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake is a consensus mechanism used by blockchain networks to validate transactions and add new blocks to the chain. Unlike PoW—used by Bitcoin—that requires miners to solve complex mathematical puzzles using powerful computers, PoS relies on validators who "stake" their own cryptocurrency as collateral. This staking process helps ensure that validators act honestly because they stand to lose their staked assets if they attempt malicious activities.
In simple terms, think of PoS as a system where your chance of being chosen to create the next block depends on how much cryptocurrency you commit or "lock up" in the network. The more you stake, the higher your chances are of being selected as a validator.
How Does Proof-of-Stake Work?
The process involves several key steps:
Validator Selection: In a PoS network, validators are chosen based on their stake—the amount of cryptocurrency they have committed. Larger stakes increase their probability of being selected to propose new blocks.
Staking Cryptocurrency: Validators lock up or "stake" their coins for a specific period as collateral. This act aligns their interests with maintaining network integrity because dishonest behavior could lead them losing their staked assets.
Creating New Blocks: When selected, validators verify transactions and assemble them into new blocks before broadcasting these blocks across the network.
Earning Rewards: Successful validation results in rewards—typically newly minted coins plus transaction fees—distributed proportionally based on each validator's stake.
This system creates an economic incentive structure that promotes honesty while reducing energy consumption compared to traditional mining methods.
Advantages of Proof-of-Stake
Proof-of-Stake offers several notable benefits:
Energy Efficiency: Since PoS does not require intensive computational work like PoW mining rigs do, it consumes significantly less electricity—a critical factor amid growing environmental concerns surrounding cryptocurrencies.
Enhanced Scalability: With more validators able to participate simultaneously without heavy hardware requirements, many PoS-based networks can process transactions faster than traditional systems.
Decentralization Potential: While centralization risks exist if large stakeholders dominate voting power—which we'll discuss later—PoS allows broader participation since validating doesn't depend solely on expensive hardware.
Security Through Economic Incentives: Validators risk losing their staked coins if they behave maliciously or attempt fraud—a deterrent against attacks such as double-spending or manipulation attempts.
Recent Adoption Trends
Major blockchain projects have adopted or are transitioning toward proof-of-stake mechanisms due to these advantages:
Ethereum 2.0 Transition: Ethereum’s move from proof-of-work towards Ethereum 2.0 marks one of the most significant shifts in blockchain history aimed at improving scalability and reducing energy consumption.
Other Networks Using PoS: Platforms like Polkadot, Solana, Cosmos, Cardano—and many others—have implemented variations of proof-of-stake consensus algorithms successfully managing high transaction throughput with lower environmental impact.
These developments reflect industry confidence that PoS can support large-scale decentralized applications while addressing sustainability concerns associated with older models like Bitcoin’s proof-of-work system.
Challenges Facing Proof-of-Stake
Despite its benefits; however,
Centralization Risks: Large stakeholders may accumulate disproportionate influence over validator selection processes—a phenomenon known as "wealth concentration." If few entities control most stakes—they could potentially manipulate governance decisions or censor certain transactions—undermining decentralization principles fundamental to blockchain technology.
Security Vulnerabilities: Certain attack vectors unique to PoS systems exist—for example:
- Nothing-at-stake attacks: Validators might vote for multiple conflicting chains because there's little cost involved without physical resource expenditure.
- Long-range attacks: Attackers could try rewriting parts of historical data if initial security measures aren’t robust enough.
Regulatory Uncertainty: As governments scrutinize cryptocurrencies more closely—including staking practices—the regulatory landscape remains uncertain which could impact adoption rates and operational frameworks moving forward.
Emerging Trends & Future Outlook
The evolution within proof-of-stake protocols continues rapidly:
Innovations such as Delegated Proof-of-Stake (DPoS)—where token holders delegate validation rights—aim at further democratizing participation while enhancing efficiency.
Concepts like Proof-of-Stake Velocity seek solutions for centralization by factoring in how often tokens change hands rather than just total holdings alone.
As technological advancements address current limitations—for instance through better slashing mechanisms that penalize bad actors—the long-term outlook suggests increased adoption across various sectors beyond cryptocurrencies—including supply chain management and digital identity verification.
Implications for Investors & Users
For investors considering staking opportunities:
- Staking can generate passive income through rewards but also involves risks such as potential loss ("slashing") if validators act dishonestly or fail technically.
For everyday users:
- Understanding whether a platform uses proof-or-stakes helps assess its sustainability profile; eco-friendly blockchains tend toward broader acceptance among environmentally conscious communities.
Final Thoughts on Proof-and Stake Systems
Proof-and-stakes represent an innovative shift towards greener—and potentially more scalable—blockchain ecosystems compared with traditional mining-based models. While challenges remain around decentralization security vulnerabilities—and regulatory clarity—the ongoing development indicates strong momentum toward mainstream adoption across various industries worldwide.
Keywords: Blockchain consensus mechanisms | Cryptocurrency validation | Energy-efficient blockchains | Validator staking | Blockchain scalability | Decentralized finance (DeFi) security


JCUSER-WVMdslBw
2025-05-22 15:45
Could you explain "Proof-of-Stake" (PoS) in simple terms?
Proof-of-Stake (PoS) Explained: A Clear Guide for Beginners and Enthusiasts
Understanding Proof-of-Stake (PoS) is essential for anyone interested in blockchain technology, cryptocurrencies, or the future of decentralized networks. As an alternative to the traditional Proof-of-Work (PoW), PoS offers a more energy-efficient and scalable way to secure blockchain networks. This article breaks down what PoS is, how it works, its advantages and challenges, recent developments, and what it means for the future of digital currencies.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake is a consensus mechanism used by blockchain networks to validate transactions and add new blocks to the chain. Unlike PoW—used by Bitcoin—that requires miners to solve complex mathematical puzzles using powerful computers, PoS relies on validators who "stake" their own cryptocurrency as collateral. This staking process helps ensure that validators act honestly because they stand to lose their staked assets if they attempt malicious activities.
In simple terms, think of PoS as a system where your chance of being chosen to create the next block depends on how much cryptocurrency you commit or "lock up" in the network. The more you stake, the higher your chances are of being selected as a validator.
How Does Proof-of-Stake Work?
The process involves several key steps:
Validator Selection: In a PoS network, validators are chosen based on their stake—the amount of cryptocurrency they have committed. Larger stakes increase their probability of being selected to propose new blocks.
Staking Cryptocurrency: Validators lock up or "stake" their coins for a specific period as collateral. This act aligns their interests with maintaining network integrity because dishonest behavior could lead them losing their staked assets.
Creating New Blocks: When selected, validators verify transactions and assemble them into new blocks before broadcasting these blocks across the network.
Earning Rewards: Successful validation results in rewards—typically newly minted coins plus transaction fees—distributed proportionally based on each validator's stake.
This system creates an economic incentive structure that promotes honesty while reducing energy consumption compared to traditional mining methods.
Advantages of Proof-of-Stake
Proof-of-Stake offers several notable benefits:
Energy Efficiency: Since PoS does not require intensive computational work like PoW mining rigs do, it consumes significantly less electricity—a critical factor amid growing environmental concerns surrounding cryptocurrencies.
Enhanced Scalability: With more validators able to participate simultaneously without heavy hardware requirements, many PoS-based networks can process transactions faster than traditional systems.
Decentralization Potential: While centralization risks exist if large stakeholders dominate voting power—which we'll discuss later—PoS allows broader participation since validating doesn't depend solely on expensive hardware.
Security Through Economic Incentives: Validators risk losing their staked coins if they behave maliciously or attempt fraud—a deterrent against attacks such as double-spending or manipulation attempts.
Recent Adoption Trends
Major blockchain projects have adopted or are transitioning toward proof-of-stake mechanisms due to these advantages:
Ethereum 2.0 Transition: Ethereum’s move from proof-of-work towards Ethereum 2.0 marks one of the most significant shifts in blockchain history aimed at improving scalability and reducing energy consumption.
Other Networks Using PoS: Platforms like Polkadot, Solana, Cosmos, Cardano—and many others—have implemented variations of proof-of-stake consensus algorithms successfully managing high transaction throughput with lower environmental impact.
These developments reflect industry confidence that PoS can support large-scale decentralized applications while addressing sustainability concerns associated with older models like Bitcoin’s proof-of-work system.
Challenges Facing Proof-of-Stake
Despite its benefits; however,
Centralization Risks: Large stakeholders may accumulate disproportionate influence over validator selection processes—a phenomenon known as "wealth concentration." If few entities control most stakes—they could potentially manipulate governance decisions or censor certain transactions—undermining decentralization principles fundamental to blockchain technology.
Security Vulnerabilities: Certain attack vectors unique to PoS systems exist—for example:
- Nothing-at-stake attacks: Validators might vote for multiple conflicting chains because there's little cost involved without physical resource expenditure.
- Long-range attacks: Attackers could try rewriting parts of historical data if initial security measures aren’t robust enough.
Regulatory Uncertainty: As governments scrutinize cryptocurrencies more closely—including staking practices—the regulatory landscape remains uncertain which could impact adoption rates and operational frameworks moving forward.
Emerging Trends & Future Outlook
The evolution within proof-of-stake protocols continues rapidly:
Innovations such as Delegated Proof-of-Stake (DPoS)—where token holders delegate validation rights—aim at further democratizing participation while enhancing efficiency.
Concepts like Proof-of-Stake Velocity seek solutions for centralization by factoring in how often tokens change hands rather than just total holdings alone.
As technological advancements address current limitations—for instance through better slashing mechanisms that penalize bad actors—the long-term outlook suggests increased adoption across various sectors beyond cryptocurrencies—including supply chain management and digital identity verification.
Implications for Investors & Users
For investors considering staking opportunities:
- Staking can generate passive income through rewards but also involves risks such as potential loss ("slashing") if validators act dishonestly or fail technically.
For everyday users:
- Understanding whether a platform uses proof-or-stakes helps assess its sustainability profile; eco-friendly blockchains tend toward broader acceptance among environmentally conscious communities.
Final Thoughts on Proof-and Stake Systems
Proof-and-stakes represent an innovative shift towards greener—and potentially more scalable—blockchain ecosystems compared with traditional mining-based models. While challenges remain around decentralization security vulnerabilities—and regulatory clarity—the ongoing development indicates strong momentum toward mainstream adoption across various industries worldwide.
Keywords: Blockchain consensus mechanisms | Cryptocurrency validation | Energy-efficient blockchains | Validator staking | Blockchain scalability | Decentralized finance (DeFi) security
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
📣 Token $JU officially surpassed the $18 mark, setting a new all-time high (ATH) and is trading at $18.56! 🚀
🔗 Trade now: http://jucoin.com/trade/ju_usdt
👉 Register for JuCoin now: https://bit.ly/3BVxlZ2
🔥 The power of the community and the #JuCoin ecosystem is booming.
#JuCoin #JuCoinVietnam #JUtoken #ATH #Layer1 #Blockchain #Crypto #Web3 #Altcoin #CryptoUpdate


Lee Jucoin
2025-08-18 06:27
📣Token $JU officially surpassed the $18 mark, setting a new all-time high (ATH)!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Miran est connu pour son soutien affiché à $BTC, avec son désormais culte : *“#Bitcoin fixes this”*.
Un défenseur du Web3 à la table du FOMC ? Le narratif devient réalité.
#Bitcoin #CryptoPolicy #BTC



Carmelita
2025-08-07 21:15
🚨 Trump propose Stephen Miran, économiste pro-Bitcoin, pour le poste de gouverneur à la Fed.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Understanding Beta: A Key Measure of Market Sensitivity
Beta is a fundamental concept in finance that helps investors understand how sensitive a security or portfolio is to movements in the overall market. It quantifies the degree to which an asset's price fluctuates relative to market changes, providing insight into its systematic risk. This metric is integral to modern portfolio theory (MPT), enabling investors to assess potential risks and returns more accurately.
In essence, beta acts as a gauge of volatility compared to the broader market index, such as the S&P 500. A beta value of 1 indicates that the security tends to move in tandem with the market—if the market rises or falls by 10%, so does this asset. A beta greater than 1 suggests higher volatility; for example, a beta of 1.5 implies that when the market increases by 10%, this security might increase by approximately 15%. Conversely, a beta less than 1 indicates lower sensitivity; for instance, a beta of 0.5 means it moves only half as much as the overall market.
Understanding what beta represents allows investors and financial analysts to evaluate how individual securities contribute to overall portfolio risk and performance. It also plays an essential role in constructing diversified portfolios aimed at balancing risk exposure against expected returns.
How Is Beta Calculated?
The calculation of beta involves statistical measures derived from historical return data:
- Covariance between an asset’s returns and those of the overall market.
- Variance of the market’s returns.
Mathematically, it is expressed as:
Beta = Covariance (Asset Returns, Market Returns) / Variance (Market Returns)This formula captures how closely an asset's price movements are linked with broader economic trends represented by benchmark indices like stocks or cryptocurrencies markets.
Financial platforms often provide pre-calculated betas based on extensive historical data analysis. However, it's important for investors and analysts to recognize that past performance does not always predict future behavior—especially in highly volatile markets like cryptocurrencies where rapid shifts can occur due to external factors such as regulatory news or technological developments.
The Role of Market Sensitivity in Investment Strategies
Market sensitivity directly influences investment decisions because it reflects how much an asset's value responds during different phases of economic cycles:
- Risk Assessment: High-beta assets tend to be more volatile but offer higher potential returns during bullish periods.
- Diversification: Combining low-beta assets with high-beta ones can help balance risk within a portfolio.
- Performance Benchmarking: Comparing an investment’s actual return against its expected movement based on its beta provides insights into managerial skill or mispricing.
Investors aiming for aggressive growth may prefer high-beta securities because they amplify gains when markets perform well but come with increased downside risks during downturns. Conversely, conservative investors might favor low-beta investments that tend not to fluctuate wildly even amid turbulent markets.
By understanding these dynamics through beta analysis, investors can tailor their strategies according to their risk tolerance levels while aligning with long-term financial goals.
Beta Beyond Traditional Markets: Focus on Cryptocurrencies
While initially developed for traditional stock markets, recent years have seen increasing application of beta analysis within cryptocurrency investing—a sector characterized by extreme volatility and rapid innovation. Cryptocurrencies like Bitcoin and Ethereum exhibit significant price swings driven by factors such as technological updates (e.g., network upgrades), regulatory developments across jurisdictions, macroeconomic trends affecting fiat currencies’ strength—and speculative trading behaviors fueled by social media hype.
In this context:
- Cryptocurrencies often display higher betas compared with traditional assets due primarily to their unpredictable nature.
- Regulatory uncertainty can cause sudden spikes or drops in prices—impacting their measured sensitivity.
- Technological advancements may either increase adoption (potentially lowering perceived risk) or introduce new vulnerabilities affecting stability metrics like beta.
As crypto markets mature further—with increased institutional participation—the relevance and accuracy of using measures like beta will improve but must be interpreted carefully given their unique characteristics compared with conventional equities or bonds.
Recent Trends Impacting Cryptocurrency Betas
The cryptocurrency landscape has experienced notable fluctuations over recent years:
The bull run from late 2020 through early 2021 saw Bitcoin reach all-time highs amid widespread institutional interest.
Subsequent corrections throughout late 2021 into early 2022 reflected heightened volatility driven partly by regulatory crackdowns globally and macroeconomic shifts such as rising interest rates.
These events underscore why understanding crypto-specific betas is crucial—they help quantify how sensitive digital assets are relative not just historically but also under evolving conditions influencing future performance expectations.
Risks Associated With Using Beta for Crypto Market Analysis
Applying traditional financial metrics like beta within cryptocurrency markets involves certain limitations:
Potential Pitfalls Include:
High Volatility & Manipulation: Crypto prices are susceptible not only due to genuine supply-demand dynamics but also through manipulation tactics such as pump-and-dump schemes which distort true sensitivities.
Regulatory Uncertainty: Sudden policy changes can drastically alter perceived risks—leading cryptos' betas astray from underlying fundamentals temporarily.
Limited Historical Data: Many newer cryptocurrencies lack extensive historical records necessary for reliable statistical calculations; thus estimates may be less accurate than those available for established stocks.
Despite these challenges, incorporating crypto-specific adjustments—such as shorter look-back periods or alternative measures—can improve insights derived frombeta analyses.
Managing Risks When Using Beta Metrics
To mitigate issues associated with high crypto-market volatility:
Combine multiple indicators alongsidebeta—for example , volume trends , sentiment analysis ,and macroeconomic factors .
Regularly update your calculations reflecting recent data rather than relying solely on long-term averages .
Use scenario analysis — assessing potential outcomes under different hypothetical conditions—to better understand possible sensitivities .
How Investors Can Use Beta Effectively
For both traditional equity portfolios and emerging digital assets strategies , understanding each security’sbeta helps craft balanced approaches aligned with personal risk appetite . Here are some practical tips :
Assess Risk Tolerance: Determine whether you prefer investments that amplify gains during bullish phases but also expose you more significantly during downturns—or if you favor steadier options less affected by broad-market swings .
Construct Diversified Portfolios: Mix high-betasecuritieswith lower-betasecuritiesto achieve desired exposure levels without overconcentrating on volatile segments .
Monitor Changes Over Time: Keep trackofbetavalues regularly sincemarketconditionsandassetvolatilities evolve . Adjust your holdings accordinglyto maintain alignmentwith your strategic objectives .
By integrating these practices into your investment process—including awareness about specific nuances relatedtocryptocurrencybetastakeholderscan make informed decisions rootedin soundrisk management principles .
Future Outlook: The Evolving Significance Of Beta
As financial markets continue evolving—with increasing integration between traditional finance sectorsand digital currencies—the importanceof measuringmarket sensitivity via metricslikebeta will grow stronger . Advances include :
Improved models incorporating real-time data analytics
– Enhanced tools leveraging machine learning algorithms
– Greater transparency around blockchain activity influencing valuation models
Furthermore,the ongoing maturationofcryptocurrencymarketswill likely leadto more standardized methodsfor calculatingand interpretingbetas,increasingtheir reliabilityfor both retailandinstitutionalinvestors alike.
Final Thoughts
Understanding whatbeta signifies—andhow it evaluatesa strategy’smarket sensitivity—is vitalfor making informedinvestment choices across diverseasset classes.In particular,the unique characteristicsofcryptocurrencies demand carefulapplicationand interpretationofthis metric.To navigate today’s complexfinancial landscape successfully requires combining quantitative toolslikebetawith qualitative insights aboutregulatory,trends,and technological developments.This holistic approach empowersinvestors tomaximizereturnswhilemanagingrisks effectivelyin bothtraditionalandin emergingmarkets.


JCUSER-F1IIaxXA
2025-05-10 00:27
What is Beta and how does it evaluate a strategy’s market sensitivity?
Understanding Beta: A Key Measure of Market Sensitivity
Beta is a fundamental concept in finance that helps investors understand how sensitive a security or portfolio is to movements in the overall market. It quantifies the degree to which an asset's price fluctuates relative to market changes, providing insight into its systematic risk. This metric is integral to modern portfolio theory (MPT), enabling investors to assess potential risks and returns more accurately.
In essence, beta acts as a gauge of volatility compared to the broader market index, such as the S&P 500. A beta value of 1 indicates that the security tends to move in tandem with the market—if the market rises or falls by 10%, so does this asset. A beta greater than 1 suggests higher volatility; for example, a beta of 1.5 implies that when the market increases by 10%, this security might increase by approximately 15%. Conversely, a beta less than 1 indicates lower sensitivity; for instance, a beta of 0.5 means it moves only half as much as the overall market.
Understanding what beta represents allows investors and financial analysts to evaluate how individual securities contribute to overall portfolio risk and performance. It also plays an essential role in constructing diversified portfolios aimed at balancing risk exposure against expected returns.
How Is Beta Calculated?
The calculation of beta involves statistical measures derived from historical return data:
- Covariance between an asset’s returns and those of the overall market.
- Variance of the market’s returns.
Mathematically, it is expressed as:
Beta = Covariance (Asset Returns, Market Returns) / Variance (Market Returns)This formula captures how closely an asset's price movements are linked with broader economic trends represented by benchmark indices like stocks or cryptocurrencies markets.
Financial platforms often provide pre-calculated betas based on extensive historical data analysis. However, it's important for investors and analysts to recognize that past performance does not always predict future behavior—especially in highly volatile markets like cryptocurrencies where rapid shifts can occur due to external factors such as regulatory news or technological developments.
The Role of Market Sensitivity in Investment Strategies
Market sensitivity directly influences investment decisions because it reflects how much an asset's value responds during different phases of economic cycles:
- Risk Assessment: High-beta assets tend to be more volatile but offer higher potential returns during bullish periods.
- Diversification: Combining low-beta assets with high-beta ones can help balance risk within a portfolio.
- Performance Benchmarking: Comparing an investment’s actual return against its expected movement based on its beta provides insights into managerial skill or mispricing.
Investors aiming for aggressive growth may prefer high-beta securities because they amplify gains when markets perform well but come with increased downside risks during downturns. Conversely, conservative investors might favor low-beta investments that tend not to fluctuate wildly even amid turbulent markets.
By understanding these dynamics through beta analysis, investors can tailor their strategies according to their risk tolerance levels while aligning with long-term financial goals.
Beta Beyond Traditional Markets: Focus on Cryptocurrencies
While initially developed for traditional stock markets, recent years have seen increasing application of beta analysis within cryptocurrency investing—a sector characterized by extreme volatility and rapid innovation. Cryptocurrencies like Bitcoin and Ethereum exhibit significant price swings driven by factors such as technological updates (e.g., network upgrades), regulatory developments across jurisdictions, macroeconomic trends affecting fiat currencies’ strength—and speculative trading behaviors fueled by social media hype.
In this context:
- Cryptocurrencies often display higher betas compared with traditional assets due primarily to their unpredictable nature.
- Regulatory uncertainty can cause sudden spikes or drops in prices—impacting their measured sensitivity.
- Technological advancements may either increase adoption (potentially lowering perceived risk) or introduce new vulnerabilities affecting stability metrics like beta.
As crypto markets mature further—with increased institutional participation—the relevance and accuracy of using measures like beta will improve but must be interpreted carefully given their unique characteristics compared with conventional equities or bonds.
Recent Trends Impacting Cryptocurrency Betas
The cryptocurrency landscape has experienced notable fluctuations over recent years:
The bull run from late 2020 through early 2021 saw Bitcoin reach all-time highs amid widespread institutional interest.
Subsequent corrections throughout late 2021 into early 2022 reflected heightened volatility driven partly by regulatory crackdowns globally and macroeconomic shifts such as rising interest rates.
These events underscore why understanding crypto-specific betas is crucial—they help quantify how sensitive digital assets are relative not just historically but also under evolving conditions influencing future performance expectations.
Risks Associated With Using Beta for Crypto Market Analysis
Applying traditional financial metrics like beta within cryptocurrency markets involves certain limitations:
Potential Pitfalls Include:
High Volatility & Manipulation: Crypto prices are susceptible not only due to genuine supply-demand dynamics but also through manipulation tactics such as pump-and-dump schemes which distort true sensitivities.
Regulatory Uncertainty: Sudden policy changes can drastically alter perceived risks—leading cryptos' betas astray from underlying fundamentals temporarily.
Limited Historical Data: Many newer cryptocurrencies lack extensive historical records necessary for reliable statistical calculations; thus estimates may be less accurate than those available for established stocks.
Despite these challenges, incorporating crypto-specific adjustments—such as shorter look-back periods or alternative measures—can improve insights derived frombeta analyses.
Managing Risks When Using Beta Metrics
To mitigate issues associated with high crypto-market volatility:
Combine multiple indicators alongsidebeta—for example , volume trends , sentiment analysis ,and macroeconomic factors .
Regularly update your calculations reflecting recent data rather than relying solely on long-term averages .
Use scenario analysis — assessing potential outcomes under different hypothetical conditions—to better understand possible sensitivities .
How Investors Can Use Beta Effectively
For both traditional equity portfolios and emerging digital assets strategies , understanding each security’sbeta helps craft balanced approaches aligned with personal risk appetite . Here are some practical tips :
Assess Risk Tolerance: Determine whether you prefer investments that amplify gains during bullish phases but also expose you more significantly during downturns—or if you favor steadier options less affected by broad-market swings .
Construct Diversified Portfolios: Mix high-betasecuritieswith lower-betasecuritiesto achieve desired exposure levels without overconcentrating on volatile segments .
Monitor Changes Over Time: Keep trackofbetavalues regularly sincemarketconditionsandassetvolatilities evolve . Adjust your holdings accordinglyto maintain alignmentwith your strategic objectives .
By integrating these practices into your investment process—including awareness about specific nuances relatedtocryptocurrencybetastakeholderscan make informed decisions rootedin soundrisk management principles .
Future Outlook: The Evolving Significance Of Beta
As financial markets continue evolving—with increasing integration between traditional finance sectorsand digital currencies—the importanceof measuringmarket sensitivity via metricslikebeta will grow stronger . Advances include :
Improved models incorporating real-time data analytics
– Enhanced tools leveraging machine learning algorithms
– Greater transparency around blockchain activity influencing valuation models
Furthermore,the ongoing maturationofcryptocurrencymarketswill likely leadto more standardized methodsfor calculatingand interpretingbetas,increasingtheir reliabilityfor both retailandinstitutionalinvestors alike.
Final Thoughts
Understanding whatbeta signifies—andhow it evaluatesa strategy’smarket sensitivity—is vitalfor making informedinvestment choices across diverseasset classes.In particular,the unique characteristicsofcryptocurrencies demand carefulapplicationand interpretationofthis metric.To navigate today’s complexfinancial landscape successfully requires combining quantitative toolslikebetawith qualitative insights aboutregulatory,trends,and technological developments.This holistic approach empowersinvestors tomaximizereturnswhilemanagingrisks effectivelyin bothtraditionalandin emergingmarkets.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
⏳Countdown: 4 Days! The JuCoin Million Airdrop Invitation Boost is on!
Open the event page, click “Share” to quickly invite friends, and accelerate your reward growth.
This is your last chance to overtake — don’t miss it!
👉 Quick Share: https://bit.ly/40NWXjH
👉 Đăng ký Jucoin ngay: https://www.jucoin.com/pro/PARTNER
#JuCoin #JucoinVietnam #Airdrop


Lee Jucoin
2025-08-12 11:14
JuCoin Million Airdrop Plan🚀
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How to Evaluate the Sustainability of Net Income
Understanding whether a company's net income is sustainable is essential for investors, analysts, and business leaders aiming to gauge long-term financial health. Sustainable net income indicates that a company can maintain its profitability over time without depleting resources or risking environmental and social responsibilities. This article explores key factors, recent trends, and practical methods to assess the sustainability of net income effectively.
What Does Sustainability in Net Income Mean?
Sustainability in net income refers to a company's ability to generate consistent profits over an extended period while balancing economic viability with environmental stewardship and social responsibility. Unlike short-term earnings spikes driven by one-off events or market anomalies, sustainable net income reflects underlying operational strength and strategic resilience.
Achieving this balance involves evaluating not just financial metrics but also how environmental practices and societal impacts influence long-term performance. Investors increasingly prioritize companies that demonstrate responsible management of resources alongside steady profitability.
Key Financial Indicators for Assessing Sustainability
Financial health forms the foundation of sustainable net income. Several indicators help determine whether a company's profits are likely to persist:
- Profitability Trends: Consistent or growing profit margins suggest stable operations capable of weathering market fluctuations.
- Cash Flow Stability: Positive cash flow ensures ongoing liquidity necessary for investments, debt repayment, and operational needs.
- Debt Levels: Maintaining manageable debt ratios prevents financial distress; excessive leverage can threaten future earnings stability.
Regular analysis of these metrics helps identify companies with resilient financial structures capable of supporting sustained profitability.
Economic Factors Influencing Long-Term Profitability
Beyond internal finances, external economic conditions significantly impact a company's ability to sustain its net income:
- Market Position & Competitive Advantage: Firms with strong brand recognition or unique offerings are better positioned for ongoing revenue streams.
- Revenue Diversification: Relying on multiple sources reduces vulnerability; if one segment underperforms, others can offset losses.
- Regulatory Environment Compliance: Adherence to laws minimizes legal risks and potential penalties that could erode profits.
Monitoring these factors provides insight into how well-positioned a company is within its industry landscape for enduring success.
The Role of Environmental Responsibility in Financial Sustainability
Environmental considerations are increasingly integral when assessing long-term profitability. Companies investing in green initiatives—such as renewable energy adoption or waste reduction—can lower operational costs while enhancing reputation among eco-conscious consumers.
Supply chain management also plays a crucial role; environmentally responsible sourcing mitigates risks related to resource depletion or regulatory sanctions due to unsustainable practices. Incorporating sustainability into core strategies not only benefits society but also supports stable profit generation by reducing exposure to environmental liabilities.
Recent Developments Impacting Net Income Sustainability
Recent corporate reports highlight contrasting scenarios illustrating the importance of sustainability:
In early 2025, Check Point Software Technologies showcased robust financial results exceeding expectations during Q1 2025[1]. Their strong earnings reflect effective management strategies aligned with both growth objectives and sustainability principles.
Conversely, Everest Group experienced challenges during the same period[2], reporting an increased combined ratio (102.7%), signaling potential strain on their profitability margins which could threaten future earnings stability if trends persist.
These examples underscore how current performance metrics serve as vital indicators when evaluating long-term viability — emphasizing the need for continuous monitoring beyond surface-level figures.
Risks That Threaten Net Income Longevity
Several risks can undermine efforts toward maintaining sustainable profits:
Financial Distress from High Debt Levels: Excessive borrowing hampers flexibility; interest obligations may divert funds from growth initiatives.
Regulatory Penalties & Non-compliance: Failure to meet environmental standards exposes firms to fines that directly reduce profit margins.
Environmental & Reputational Risks: Environmental damage incidents can lead not only legal consequences but also loss of customer trust impacting sales longevity.
Proactively managing these risks through strategic planning enhances resilience against unforeseen disruptions affecting long-term earnings stability.
Practical Strategies for Evaluating Net Income Sustainability
To accurately assess whether a company's profits are sustainable over time:
- Analyze historical financial statements focusing on profit consistency and cash flow patterns.
- Review industry position—market share data—and diversification strategies employed by the firm.
- Examine corporate social responsibility (CSR) reports highlighting green initiatives and supply chain ethics.
- Monitor regulatory compliance records alongside any penalties incurred historically.
- Stay updated on macroeconomic trends influencing sector-specific demand cycles or resource availability.
Combining quantitative data with qualitative insights offers a comprehensive view essential for informed decision-making regarding investment or strategic planning.
Keywords:sustainable net income | financial health | economic sustainability | environmental impact | cash flow analysis | risk assessment | corporate responsibility | long-term profitability


JCUSER-F1IIaxXA
2025-05-19 17:00
How to evaluate the sustainability of net income?
How to Evaluate the Sustainability of Net Income
Understanding whether a company's net income is sustainable is essential for investors, analysts, and business leaders aiming to gauge long-term financial health. Sustainable net income indicates that a company can maintain its profitability over time without depleting resources or risking environmental and social responsibilities. This article explores key factors, recent trends, and practical methods to assess the sustainability of net income effectively.
What Does Sustainability in Net Income Mean?
Sustainability in net income refers to a company's ability to generate consistent profits over an extended period while balancing economic viability with environmental stewardship and social responsibility. Unlike short-term earnings spikes driven by one-off events or market anomalies, sustainable net income reflects underlying operational strength and strategic resilience.
Achieving this balance involves evaluating not just financial metrics but also how environmental practices and societal impacts influence long-term performance. Investors increasingly prioritize companies that demonstrate responsible management of resources alongside steady profitability.
Key Financial Indicators for Assessing Sustainability
Financial health forms the foundation of sustainable net income. Several indicators help determine whether a company's profits are likely to persist:
- Profitability Trends: Consistent or growing profit margins suggest stable operations capable of weathering market fluctuations.
- Cash Flow Stability: Positive cash flow ensures ongoing liquidity necessary for investments, debt repayment, and operational needs.
- Debt Levels: Maintaining manageable debt ratios prevents financial distress; excessive leverage can threaten future earnings stability.
Regular analysis of these metrics helps identify companies with resilient financial structures capable of supporting sustained profitability.
Economic Factors Influencing Long-Term Profitability
Beyond internal finances, external economic conditions significantly impact a company's ability to sustain its net income:
- Market Position & Competitive Advantage: Firms with strong brand recognition or unique offerings are better positioned for ongoing revenue streams.
- Revenue Diversification: Relying on multiple sources reduces vulnerability; if one segment underperforms, others can offset losses.
- Regulatory Environment Compliance: Adherence to laws minimizes legal risks and potential penalties that could erode profits.
Monitoring these factors provides insight into how well-positioned a company is within its industry landscape for enduring success.
The Role of Environmental Responsibility in Financial Sustainability
Environmental considerations are increasingly integral when assessing long-term profitability. Companies investing in green initiatives—such as renewable energy adoption or waste reduction—can lower operational costs while enhancing reputation among eco-conscious consumers.
Supply chain management also plays a crucial role; environmentally responsible sourcing mitigates risks related to resource depletion or regulatory sanctions due to unsustainable practices. Incorporating sustainability into core strategies not only benefits society but also supports stable profit generation by reducing exposure to environmental liabilities.
Recent Developments Impacting Net Income Sustainability
Recent corporate reports highlight contrasting scenarios illustrating the importance of sustainability:
In early 2025, Check Point Software Technologies showcased robust financial results exceeding expectations during Q1 2025[1]. Their strong earnings reflect effective management strategies aligned with both growth objectives and sustainability principles.
Conversely, Everest Group experienced challenges during the same period[2], reporting an increased combined ratio (102.7%), signaling potential strain on their profitability margins which could threaten future earnings stability if trends persist.
These examples underscore how current performance metrics serve as vital indicators when evaluating long-term viability — emphasizing the need for continuous monitoring beyond surface-level figures.
Risks That Threaten Net Income Longevity
Several risks can undermine efforts toward maintaining sustainable profits:
Financial Distress from High Debt Levels: Excessive borrowing hampers flexibility; interest obligations may divert funds from growth initiatives.
Regulatory Penalties & Non-compliance: Failure to meet environmental standards exposes firms to fines that directly reduce profit margins.
Environmental & Reputational Risks: Environmental damage incidents can lead not only legal consequences but also loss of customer trust impacting sales longevity.
Proactively managing these risks through strategic planning enhances resilience against unforeseen disruptions affecting long-term earnings stability.
Practical Strategies for Evaluating Net Income Sustainability
To accurately assess whether a company's profits are sustainable over time:
- Analyze historical financial statements focusing on profit consistency and cash flow patterns.
- Review industry position—market share data—and diversification strategies employed by the firm.
- Examine corporate social responsibility (CSR) reports highlighting green initiatives and supply chain ethics.
- Monitor regulatory compliance records alongside any penalties incurred historically.
- Stay updated on macroeconomic trends influencing sector-specific demand cycles or resource availability.
Combining quantitative data with qualitative insights offers a comprehensive view essential for informed decision-making regarding investment or strategic planning.
Keywords:sustainable net income | financial health | economic sustainability | environmental impact | cash flow analysis | risk assessment | corporate responsibility | long-term profitability
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
